What is Device Posture Security?
Device Posture Security is a security feature that allows Organization Administrators to check and evaluate Member devices according to predefined security rules, alerting them to non-compliant devices. This functionality extends to monitoring and potentially blocking network access for accounts associated with non-compliant or untrusted devices, enhancing the security posture of an organization.
How to enable Device Posture Security functionality?
To enable Device Posture Security:
- Navigate to the Control panel and select Device security
- Head to Device Posture Security and click on Enable.
This action allows Organization Administrators to establish rules for checks to monitor and restrict access for non-compliant device accounts.
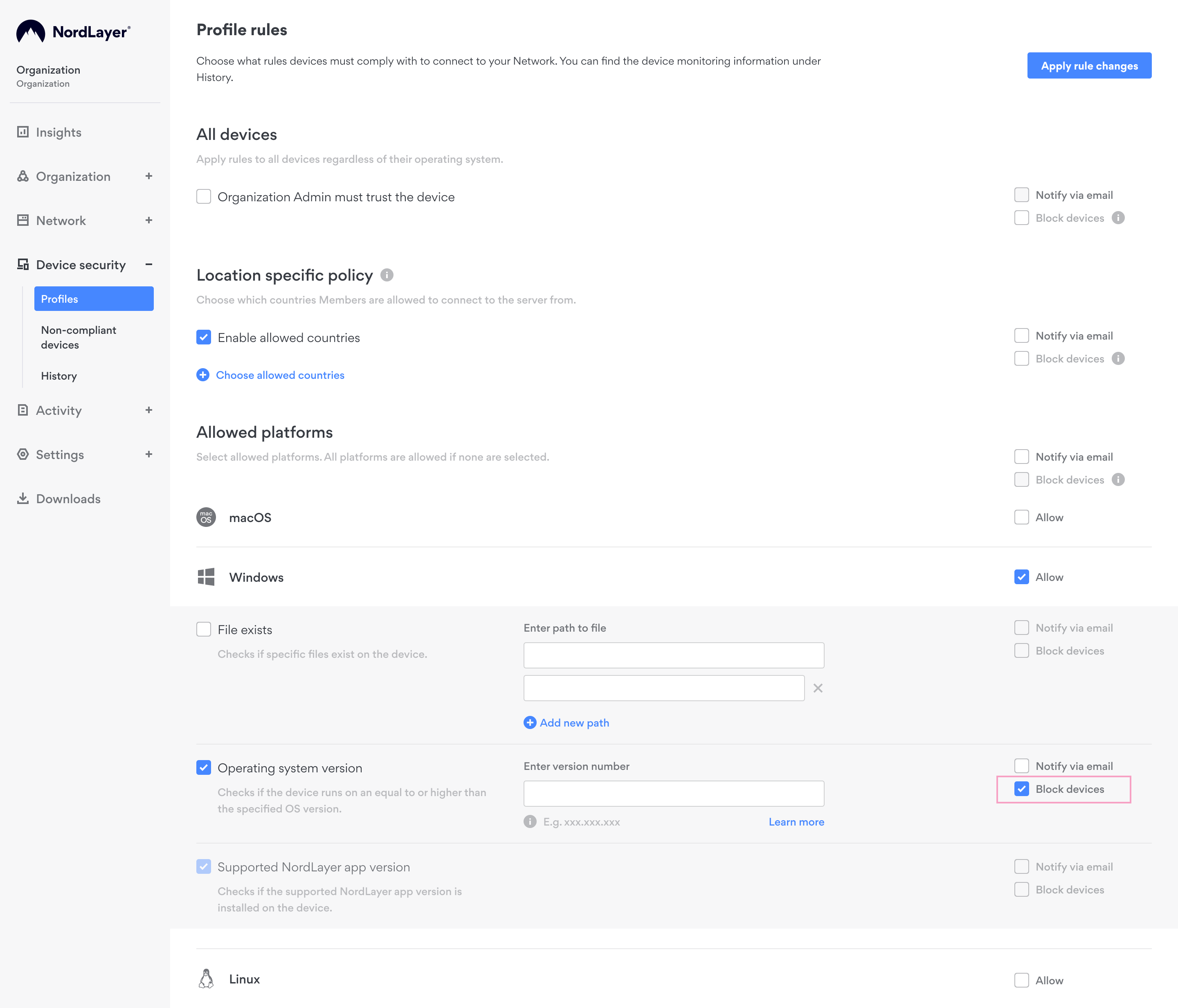
The rules include:
- Checks for the specific files on the device
- Verification of the device's operating system version
- NordLayer version checks to ensure that it's supported
- Confirmation that the device is neither jailbroken nor rooted
- Geographical location of the device
Applying these rules involves selecting the desired checks and clicking Apply rule changes.
Creating Profiles
Profiles are a set of rules that can be assigned by Organization Admins to the entire Organization.
A default Profile is currently applicable to all Members
To configure the default Profile:
- Navigate to the Control Panel
- Select Device Security
- Click on Profiles, there you can modify the default profile as per your organizational needs.
Monitoring device compliance
To monitor non-compliant devices:
- Navigate to the Control Panel
- Select Device Security
- Click on Non-compliant devices, there you can modify the default profile as per your organizational needs.
By following these steps, you can ensure that your organization's devices are uniformly secured and compliant with your security protocols.
Blocking non-compliant devices
Ensuring only compliant devices can access your network is crucial for maintaining security. Follow these steps to restrict access effectively:
- Navigate to the Control Panel
- Select Device Security
- Click on Profiles
- Tick the checkbox Block devices next to the specific rules that you want to block
Monitoring history
Keeping track of device compliance over time can help you identify patterns and potential security risks. Here's how to access the monitoring history:
- Start by going to the Control Panel and select Device Security
- To see a log of all monitored activities and device compliance statuses, click on History.
This will show you a detailed record of device interactions with your network.
What are untrusted devices and non-compliant devices?
An untrusted device refers to a new device attempting to connect to the network without the approval of Organization Administrators. To convert an untrusted device into a trusted one, Organization Administrators can select Trust this device button, adjacent to the device's listing.
A non-compliant device, on the other hand, fails to adhere to established rules.
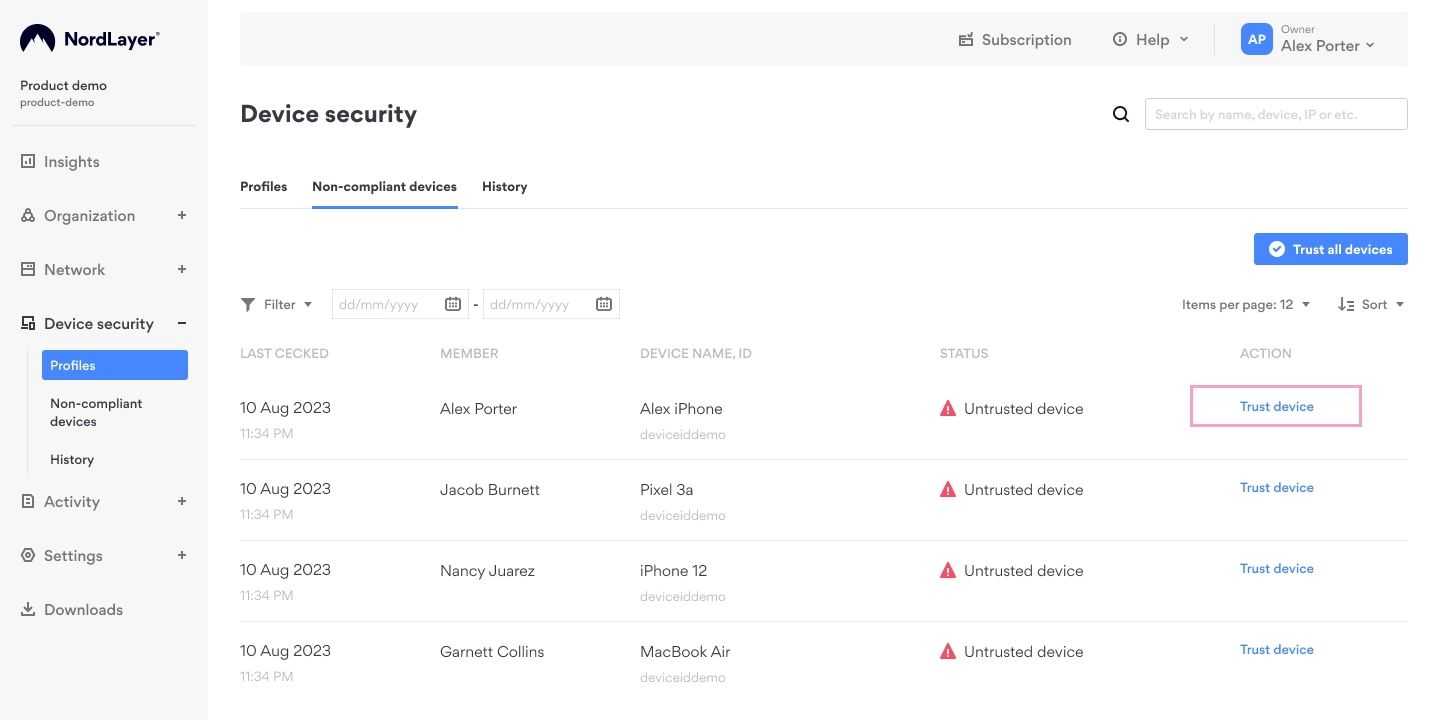
A non-compliant device is a device that doesn’t comply with the set rules.
If the Organization Admin must trust the device setting is enabled, you can choose to trust either one device or multiple devices simultaneously. This action will change their status from Untrusted device to Trusted during the subsequent device posture check.
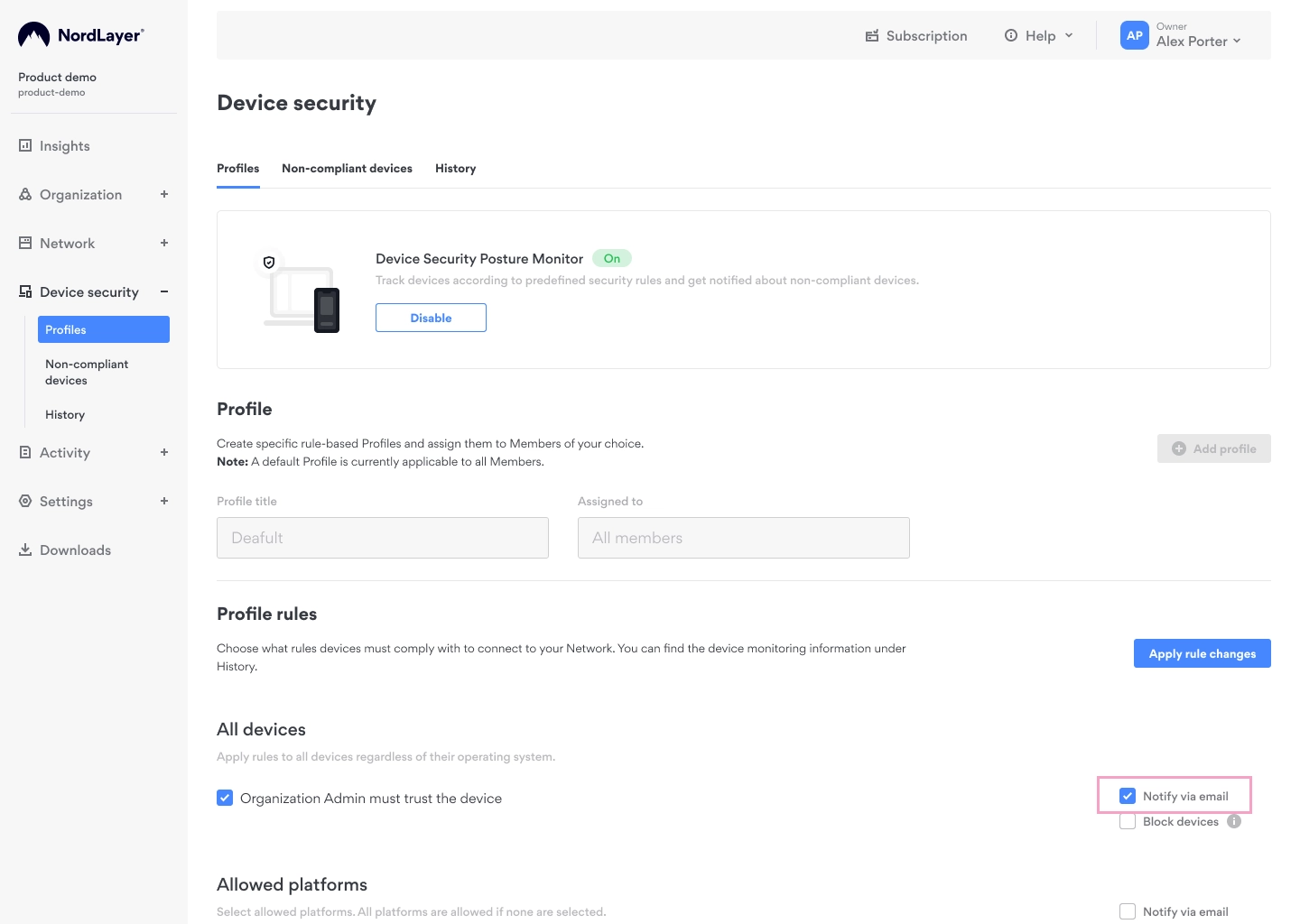
How do email notifications and compliance re-evaluation work?
To receive email alerts when devices not meeting your network's compliance standards connect, follow these steps:
- Navigate to the Control Panel
- Select Device Security
- Click on Profiles
- Tick the Notify via email option adjacent to the selected rules within the control panel.
To initiate a re-assessment of your device's compliance status, open the NordLayer application and select Check again. This action starts the re-evaluation process, which typically concludes within a few minutes.
Note: In case you have any questions or are experiencing any issues, please feel free to contact our 24/7 customer support team.