Note: If your device/service supports SHA256 and DH group 14, it is recommended to use these settings instead.
pfSense IPsec Site-to-Site VPN tunnel configuration
-
Go to VPN -> IPsec
-
Select +Add P1
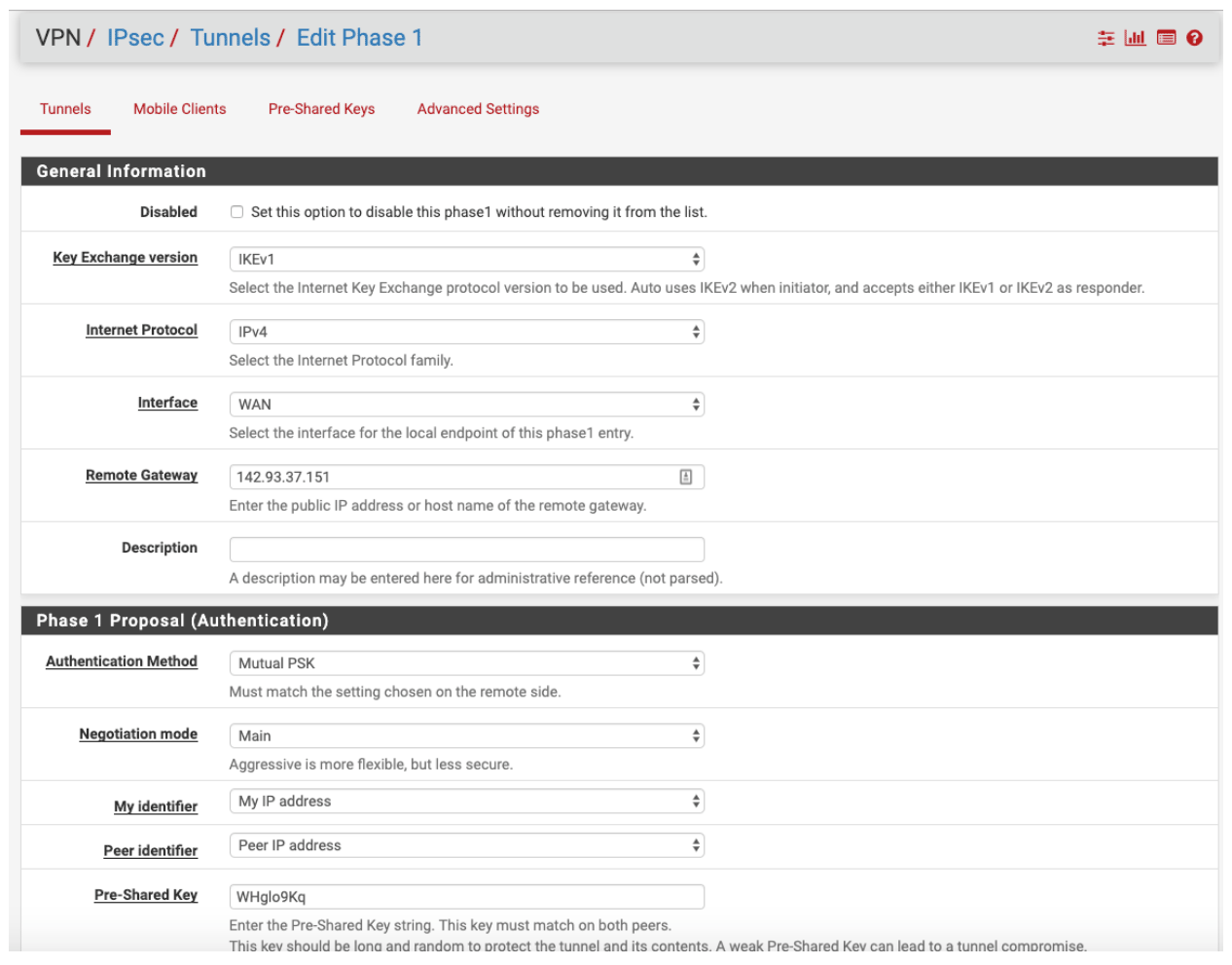
- Key Exchange Version: IKEv2
- Internet Protocol: IPv4
- Interface: Your pfSense WAN Interface
- Remote Gateway: the IP of your NordLayer server with a dedicated IP
- Authentication Method: Mutual PSK
- Negotiation Mode: Main
- My Identifier: My IP Address
- Peer Identifier: Peer IP Address
- Pre-Shared key: generate a key (we will also need this value on our end)
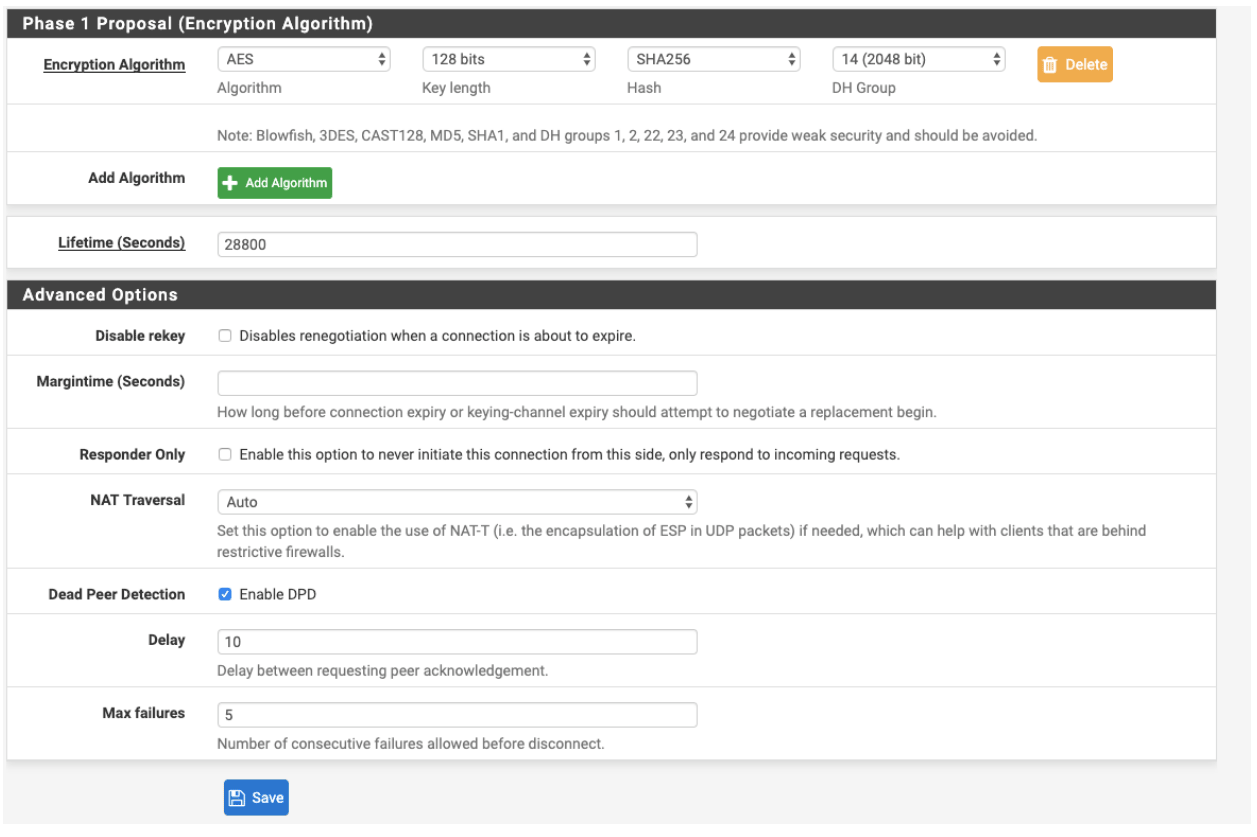
- Encryption Algorithm
- Algorithm: AES
- Key Length: 256 bits
- HASH: SHA256
- DH Group: 14
- Lifetime (Seconds): 28800
- Advanced Options
- Disable rekey: Unchecked
- Margintime (Seconds): Empty
- Responder Only: Unchecked
- NAT Traversal: Auto
- Dead Peer Detection: Checked
- Delay: 10
- Max failures: 5
- Select Save
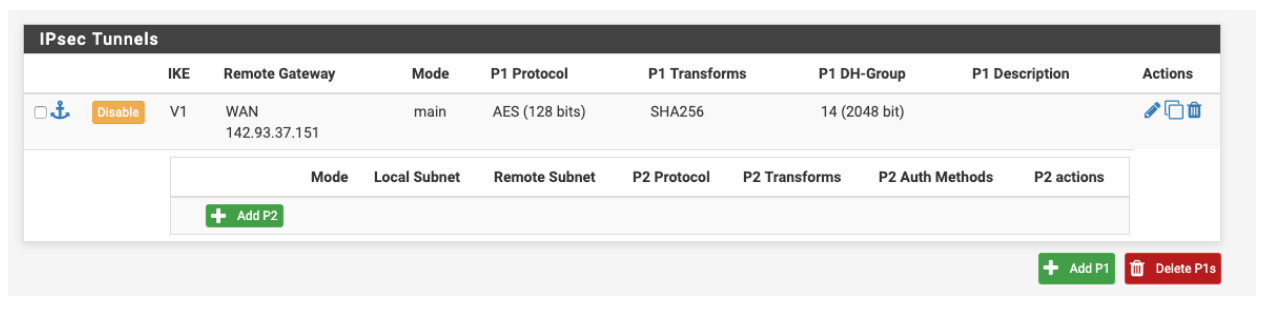
- Add phase 2: Select +Add p2
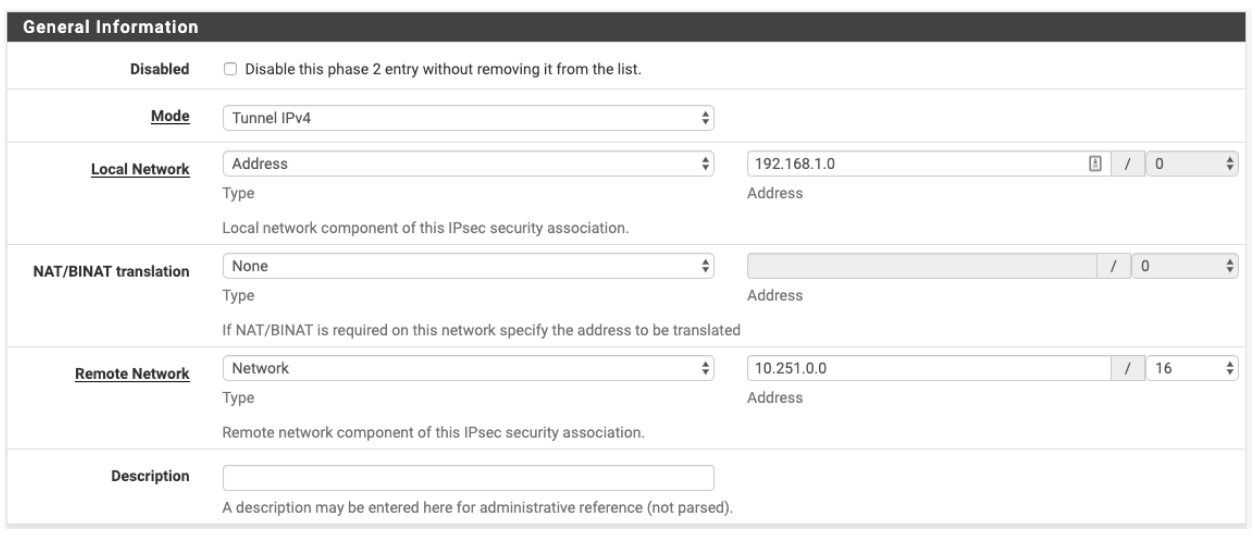
- Mode: Tunnel IPv4
- Local Network: Network: Put your local LAN network subnet
- Remote Network: Network: 10.6.0.0/20
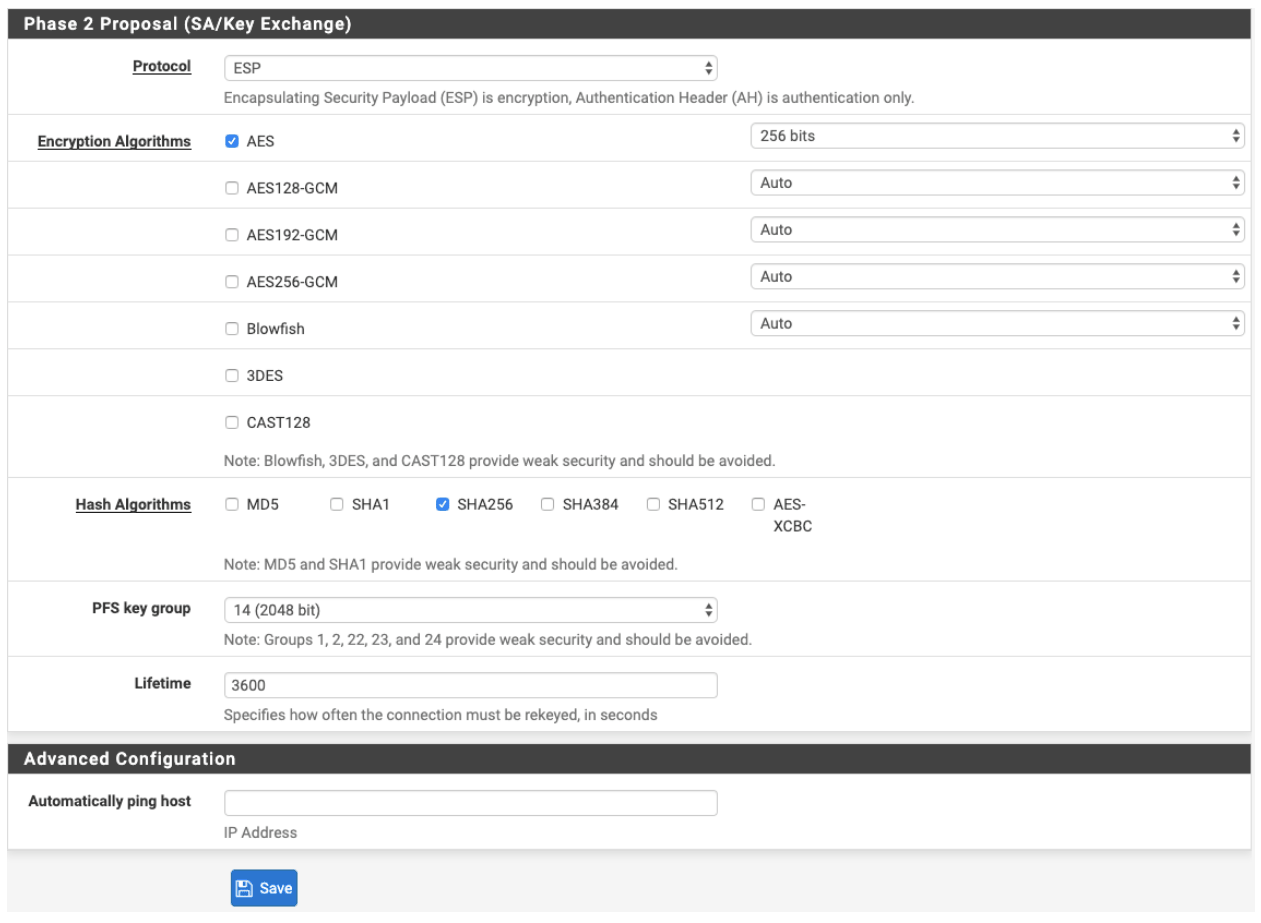
- Phase 2: Proposal
- Protocol: ESP
- Encryption Algorithm-AES: 256 bits
- Hash Algorithms: SHA256
- PFS Key Group: 14
- Lifetime (Seconds): 3600
- Select Save
- Select Apply Changes
pfSense Firewall Rules (Optional)
-
In the Menu Bar go to Firewall -> Rules
-
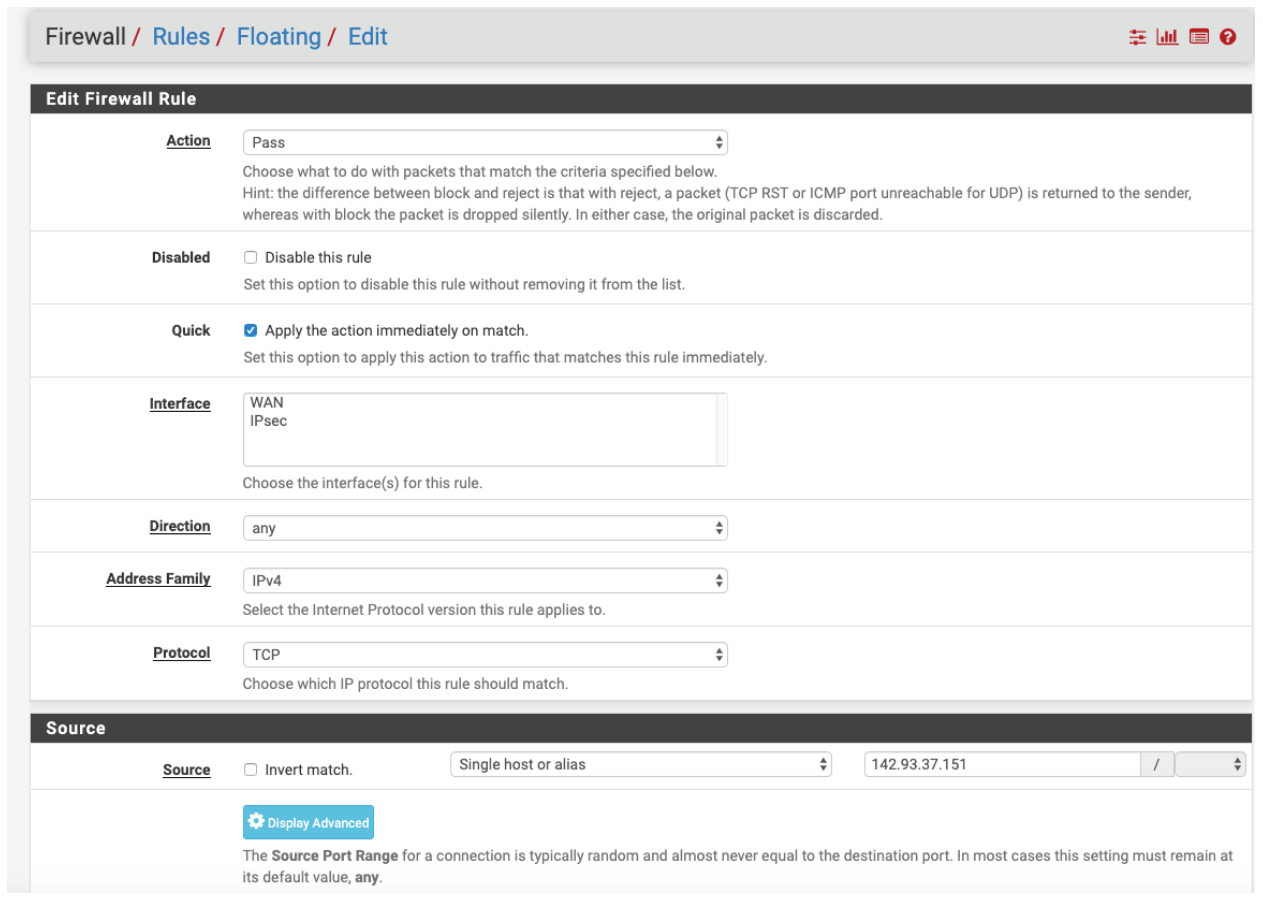
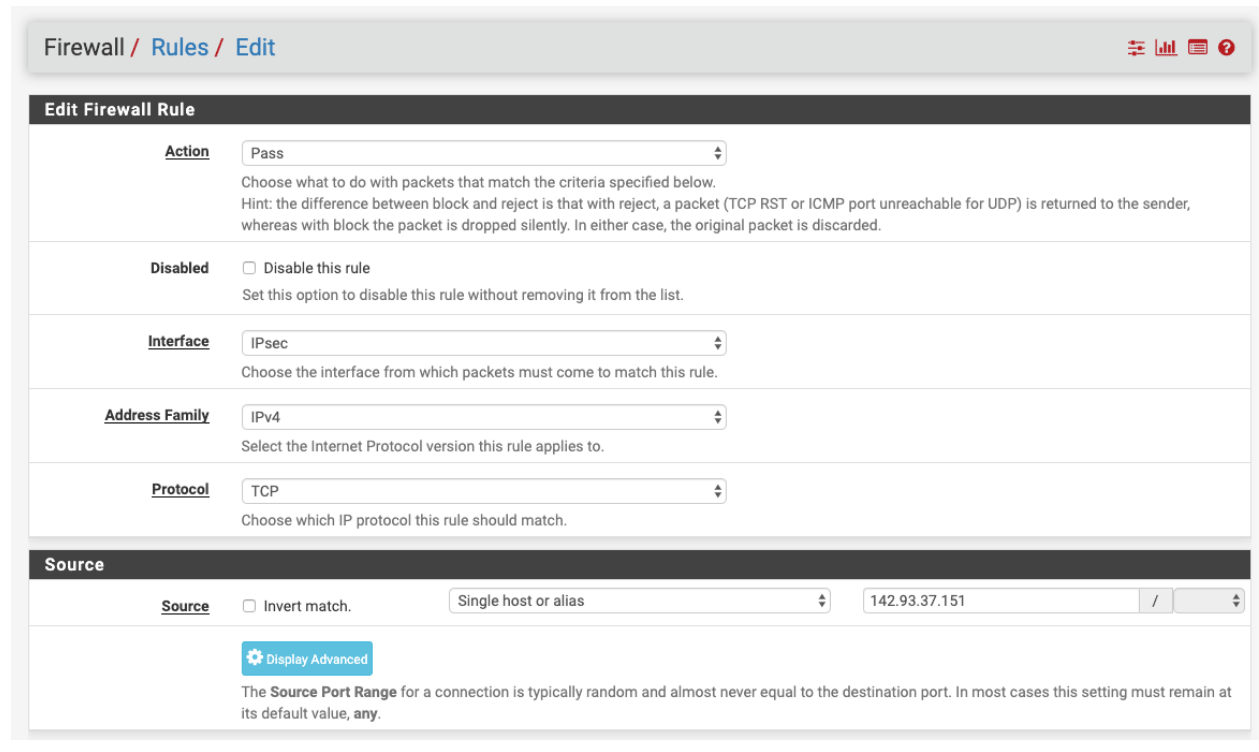
Under IPSEC add a new rule
- Action: Pass
- Quick: Mark v
- Interface: WAN and IPSEC
- Source: the IP of your NordLayer server with a dedicated IP
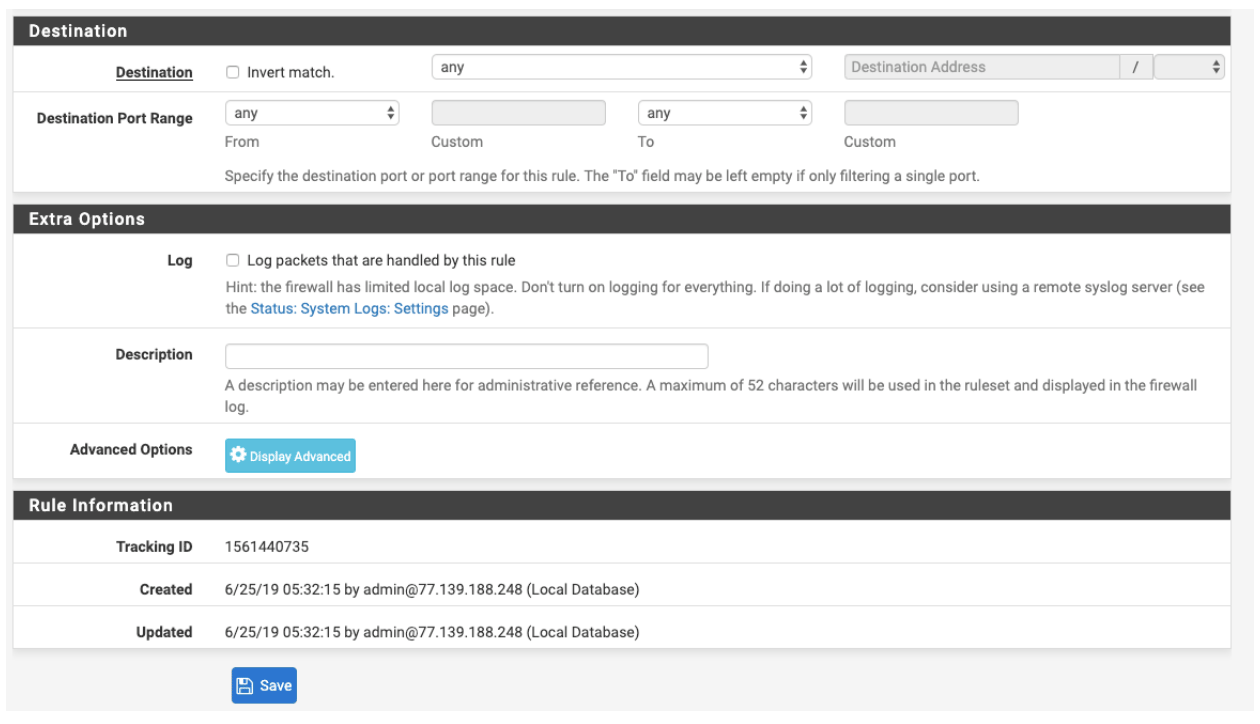
- Destination: Either put any or you can limit to your FW external IP
- Select Save.
- Under IPSEC add a new rule:
- Action: Pass
- Source: the IP of your NordLayer server with a dedicated IP
- Destination: Either put any or you can limit to your FW external IP
- Select Save.
- Select Apply Changes
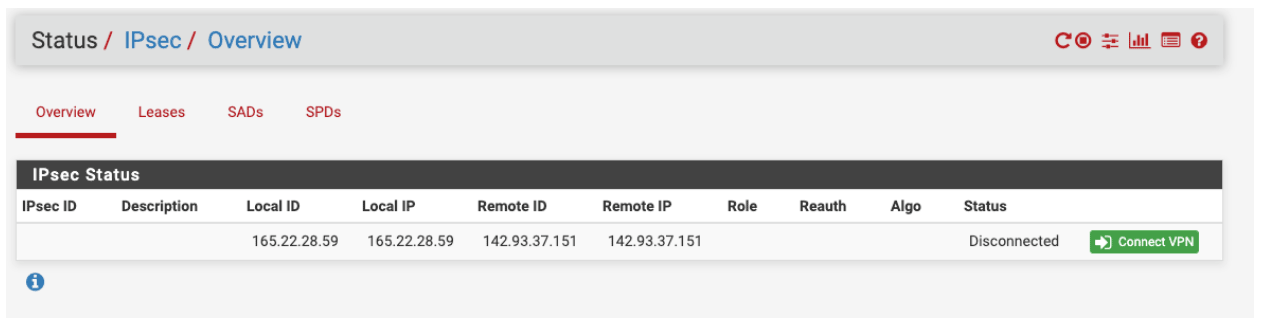
Bringing the tunnel up
-
In the Menu Bar go to Status:-> IPsec
-
On the tunnel, you created select: Connect VPN
Ending note:
In order to finalize the site-to-site setup on our end, please provide these values via Site-to-site request from in the NordLayer Control Panel:
- Pre-shared key - you can generate it or we can provide it
- Encryption details (AES, SHA and DH group) - AES256, SHA256 and DH group 14 are recommended (also must support IKEv2)
- Remote gateway/router public IP (must be reachable while connected to the server with a dedicated IP)
- Remote subnet and mask (the subnet is used in your local network)
Note: In case you are experiencing different results, make sure that you have you carefully gone through all the steps. Having said that, in case the issue persists please feel free to contact our 24/7 customer support team.