User provisioning is the IAM process of creating user accounts with specifically designated rights and permissions per the user’s role within a company. The process enables monitoring, management, and modification of the user’s account throughout their lifecycle in an organization — onboarding, promotions, transfers, and offboarding. The de-provisioning process follows, which covers deleting the account.
Entra ID is a leading user provisioning tool with which NordLayer fully integrates. Admins manage the process through a centralized platform rather than logging into their NordLayer Control Panel.
How to setup user provisioning with Entra ID
Here’s a step-by-step guide on how to set up user provisioning with NordLayer organizations and Entra ID (Azure AD):
Note: This guide is for those using the new Entra ID (Azure AD) admin panel. To switch to the new design, follow the instructions given by Entra ID.
Go to Microsoft Entra ID and log in
Go to Entra ID Active Directory
Select Enterprise applications in the left sidebar menu;
.png)
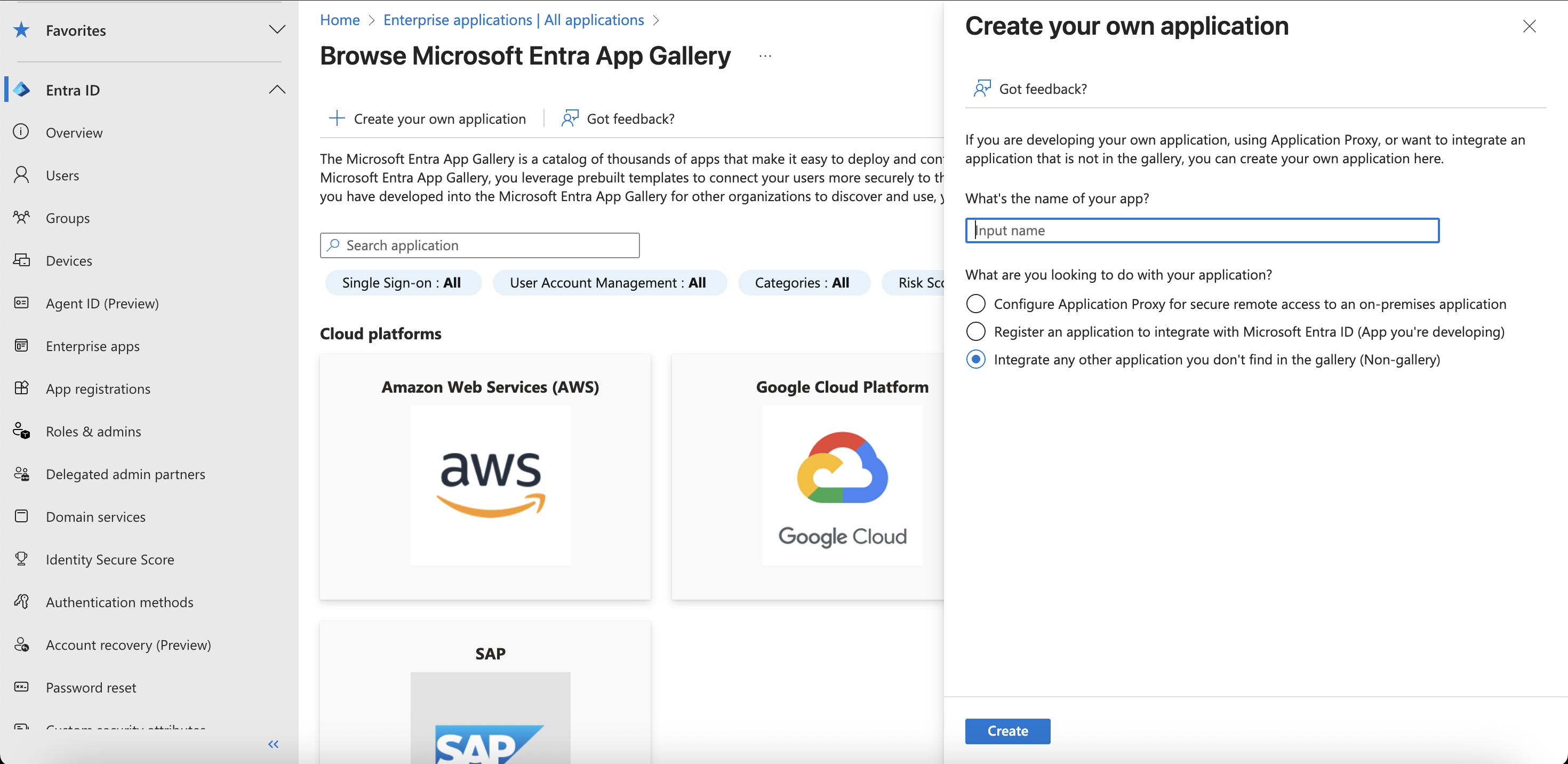
- Select New application -> Create your own application
.png)
- Enter the name of your application and choose Integrate any other application you don’t find in the gallery (Non-gallery)
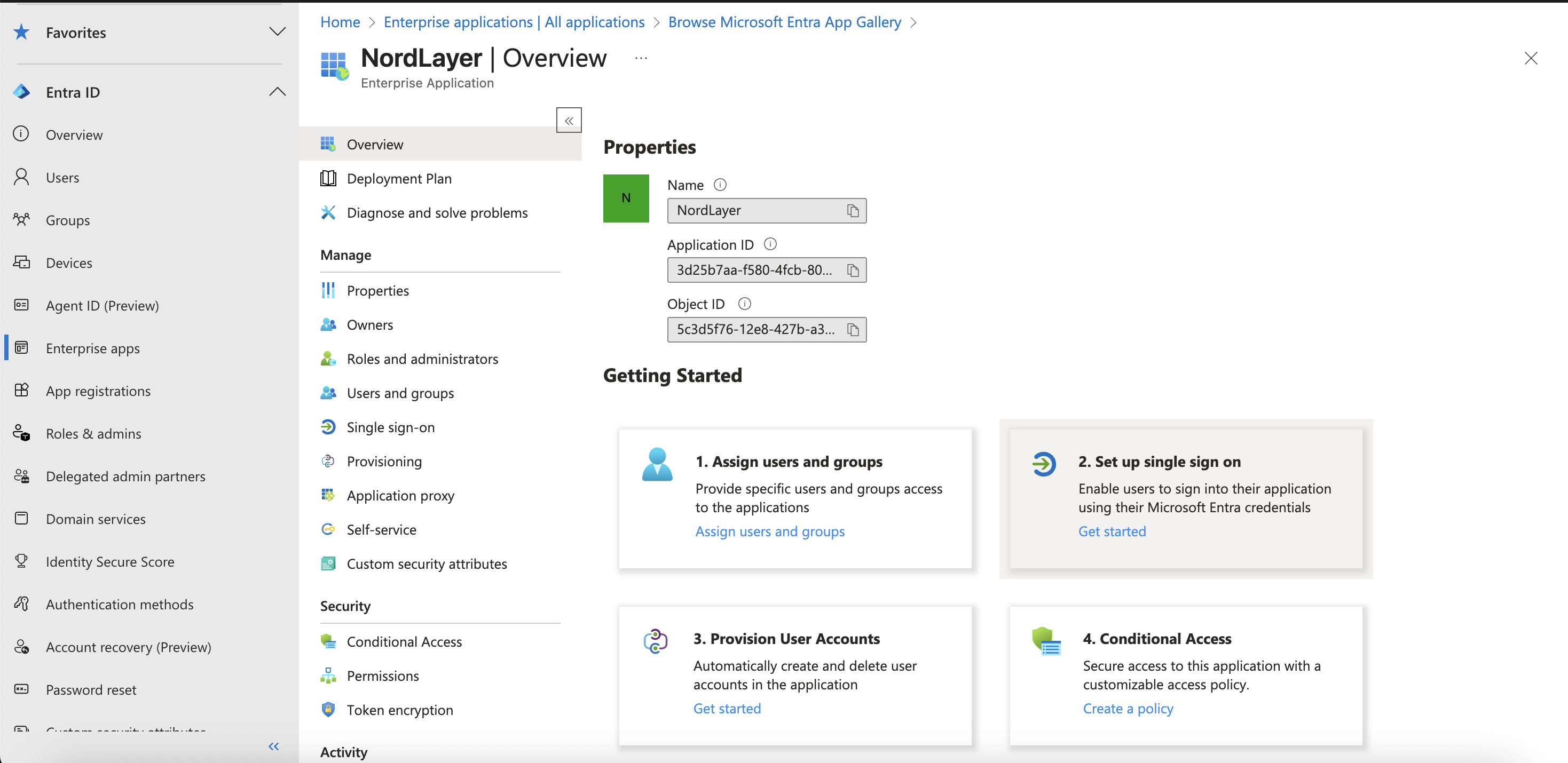
- On the application page, select Users and Groups in the left sidebar menu and add users
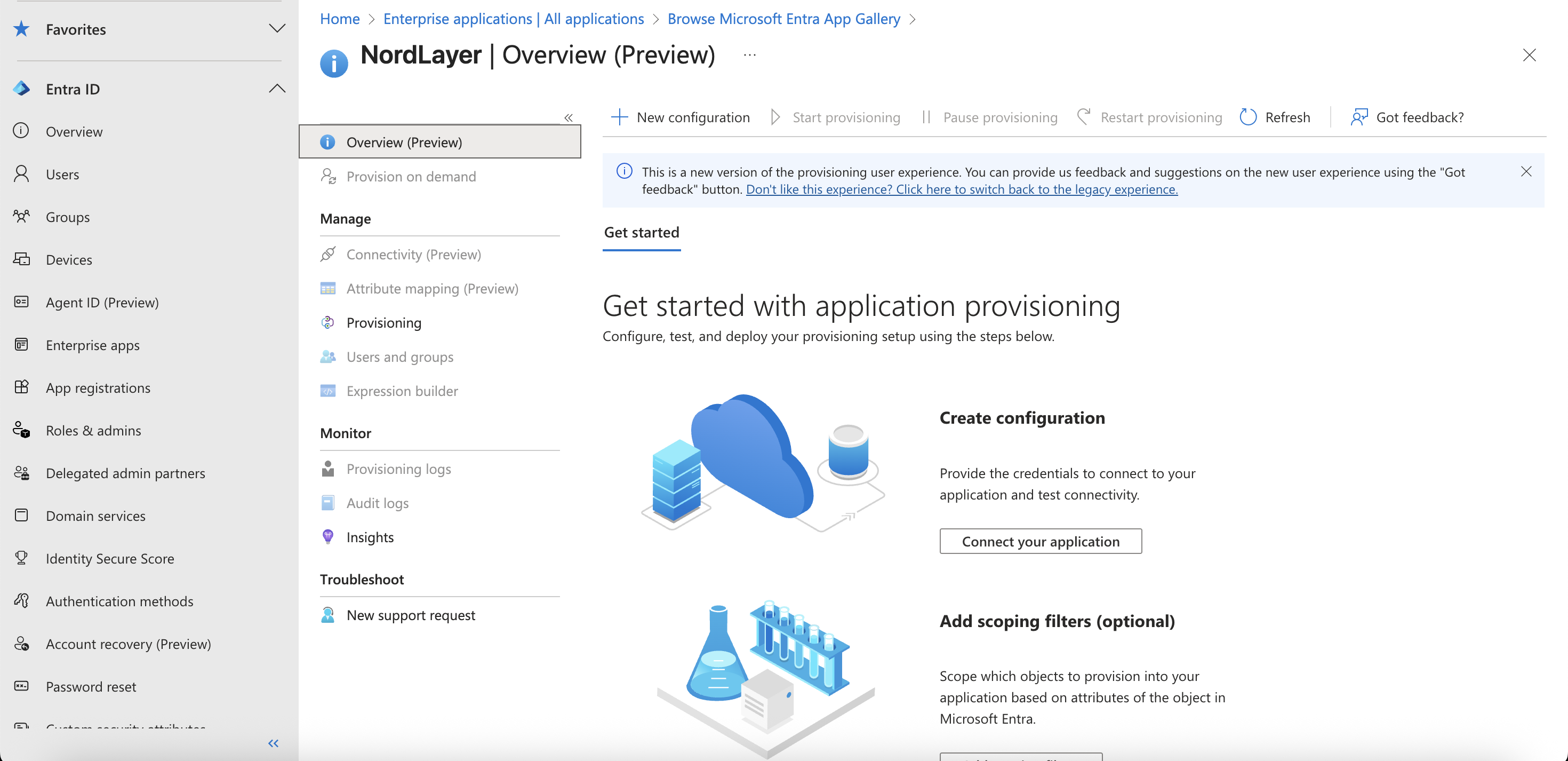
- Open Provisioning in the left sidebar menu and click Create configuration
Go to our website
Log into the NordLayer Control Panel
Go to Settings - Login methods
.jpg)
- Turn the toggle on for SCIM Provisioning with Azure AD
- In the new window (modal), you will see SCIM credentials. Copy credentials (Tenant URL & Secret token) and press Continue
Under Provisioning Mode, select Bearer authentication and enter the admin credentials you saw in the NordLayer Control Panel
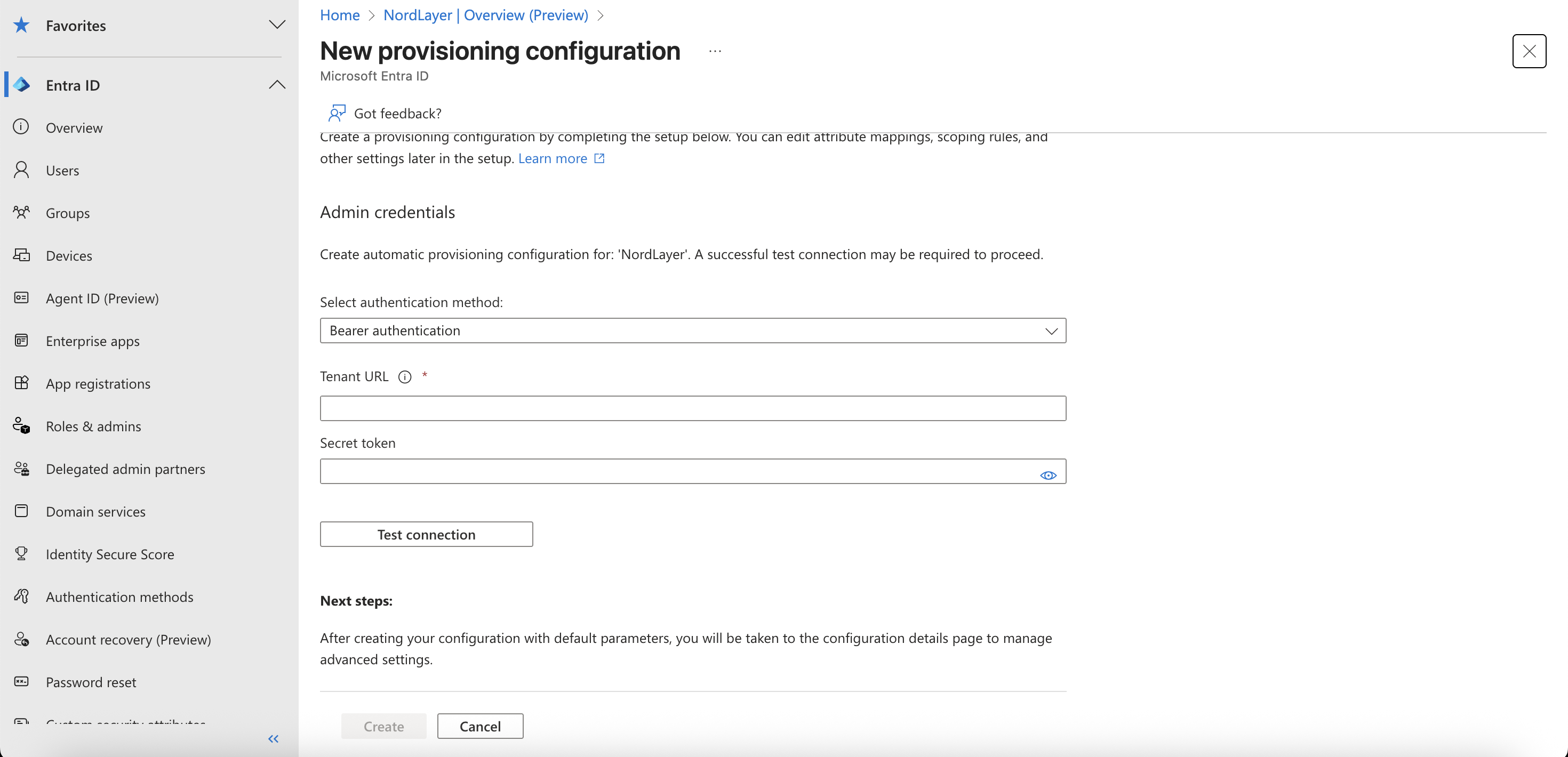
- Click Test Connection and wait while the check takes place
- Once the check is complete, click Save and then close the window
- Select Start provisioning

Beginning the user provisioning process will sync your NordLayer and Entra ID accounts.
Go back to the NordLayer Control Panel on our website, navigate to Settings - Login Methods, and set up Entra ID authentication.
Note: You can now inform your users that Azure SSO is available as a login option to the NordLayer application.
For more information visit How do I enable Entra ID 3rd party authentication?
User provisioning with Microsoft Entra ID in Control Panel
When User Provisioning with Microsoft Azure AD is enabled, it will look like this with an important message reminding you to enable Azure AD as a login method.
.jpg)
Note: Be aware that you will lose the integration between SCIM and your Control Panel if the feature is disabled or if you add new credentials to Azure settings.
Once enabled and you have provisioned at least one member or team, you will receive a message indicating that you can only edit provisioned members or teams in their source (Azure AD in this case). It means provisioned members and teams become read-only; you won’t be able to edit or delete them in the NordLayer Control Panel.
Also, provisioned members and teams will have the Windows icons on their avatar to separate them from manually created members and teams.
You can still invite members and create teams manually when this feature is enabled. It means there’s the possibility to have provisioned and manually created members and teams in your organization.
Manually created members cannot be added to provisioned teams. It means when you are inviting new members (via the “Invite new member” button in the member list), teams listed under “Assign to team (optional)” are automatically filtered to only display manually created teams.
Provisioned members can be added to manually created teams (“Create team” in teams list or “Add a member” in inner team page).
If this feature is disabled and you have provisioned members, these members will become editable. The Windows icon will still be seen on the member’s or team’s avatars to separate them.
Note: If you edited provisioned info, i.e., a team’s name, and you turn on Provisioning again, be aware Azure won’t be able to find the team and will create a new one. The same condition will apply to members if they change their email addresses.
See logged actions like turning on or off the feature and any other actions triggered by SCIM Provisioning under Activity log - Actions tab:
.jpg)
Note: In case you have any questions or are experiencing any issues, please feel free to contact our 24/7 customer support team.