- 2 Minutes to read
Setting up site-to-site on SonicWall
- 2 Minutes to read
Note: If your device/service supports SHA256 and DH group 14, it is recommended to use these settings instead.
Creating objects in SonicWall
Go to Objects in SonicWall
Go to Address Object
Select Add
Add the IP of your NordLayer dedicated server
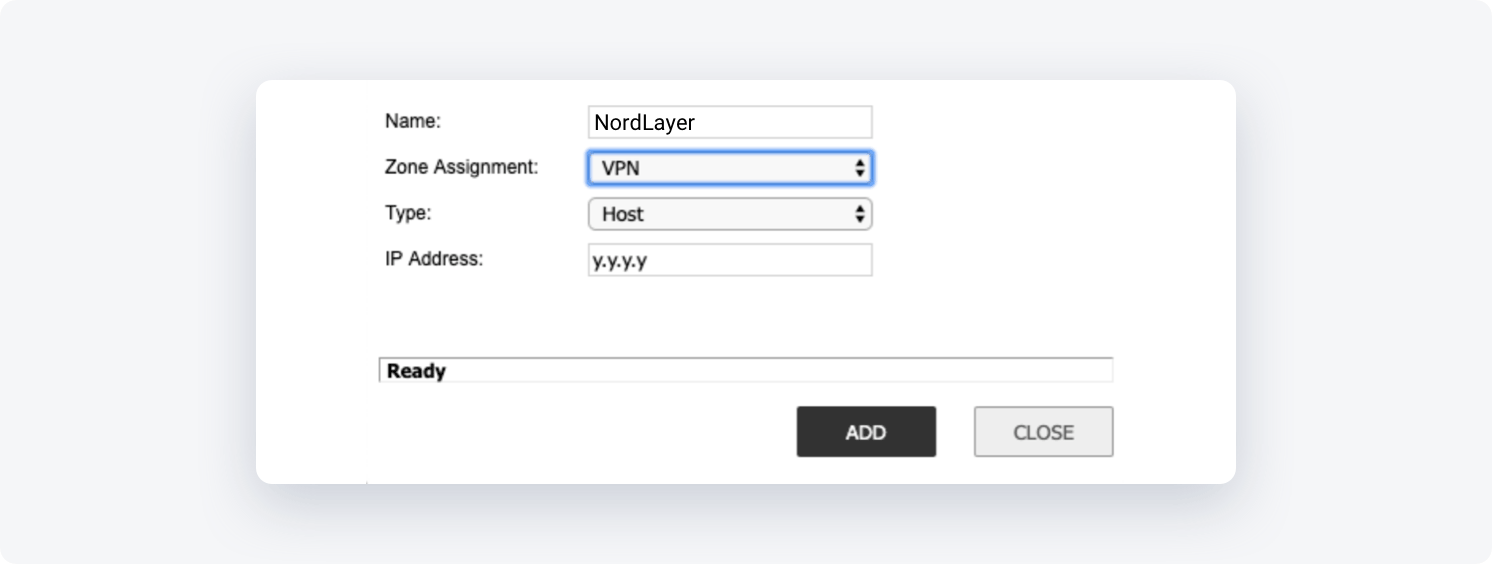
- Name: Give the object a name "NordLayer-Gateway"
- Zone Assignment: VPN
- Type: Host
- IP Address: Put the IP of your NordLayer dedicated server
- Add NordLayer Subnet Network (10.6.0.0)
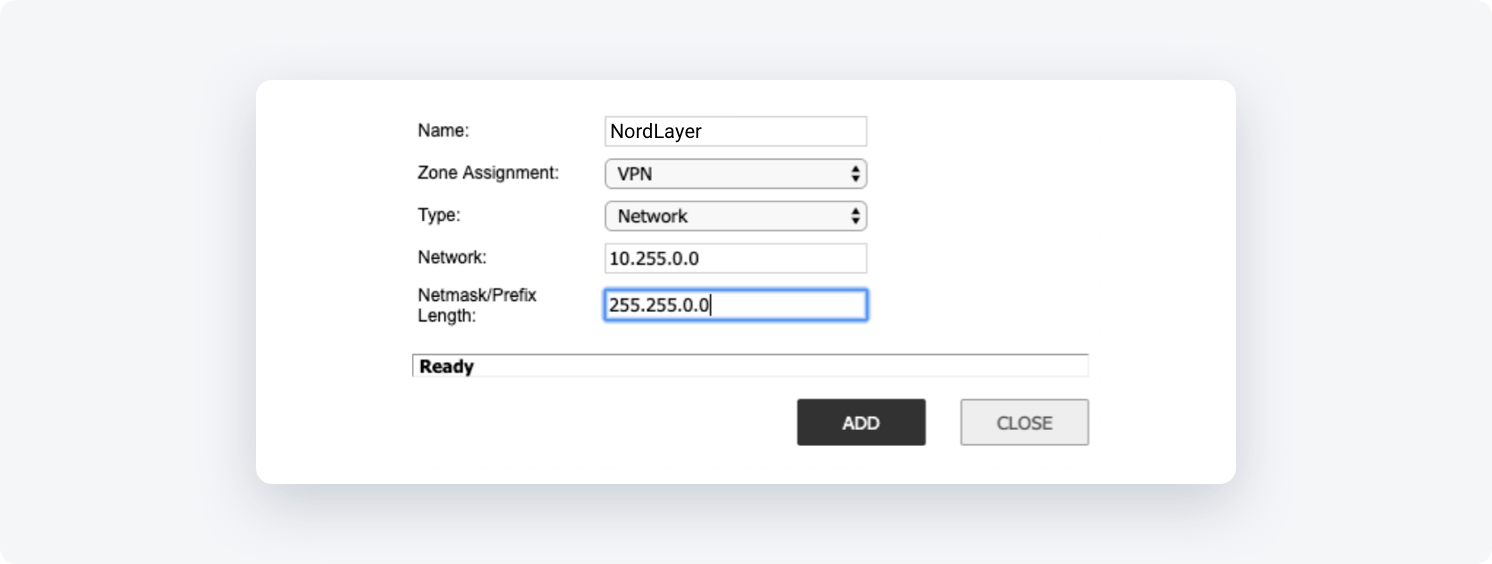
- Name: Give the object a name: "NordLayer-Network"
- Zone Assignment: VPN
- Type: Network
- Network: put 10.6.0.0
- Netmask/Prefix Length: put 255.255.240.0
Access Rule
Go to Policy:-> Rules
Select Add
First Rule to add: VPN to WAN
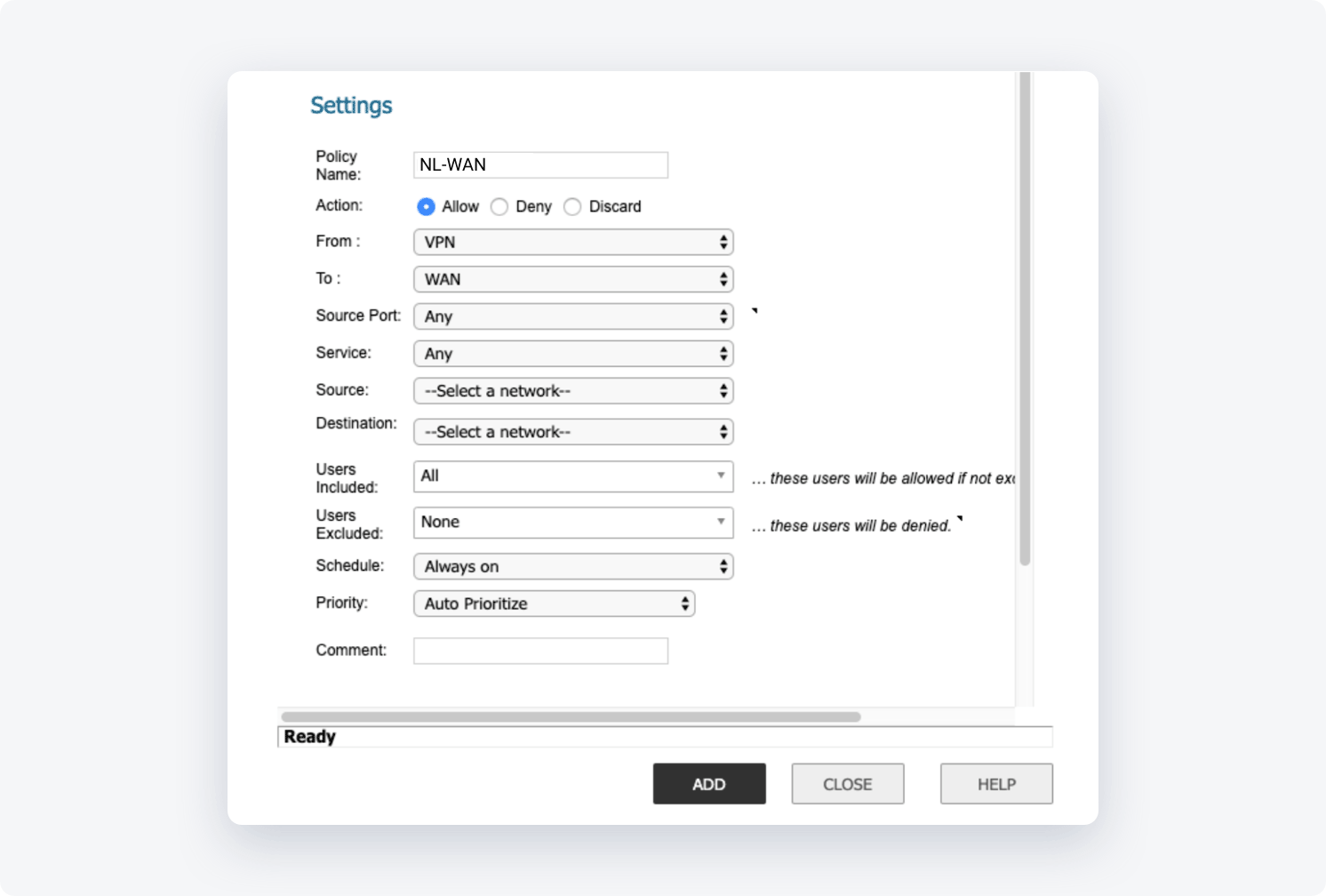
- Policy Name: NordLayer-WAN
- Action: Allow
- From: VPN
- To: WAN
- Source Port: Any
- Service: Any
- Source: NordLayer-Gateway object
- Destination: Your external internet interface object
- Select Add.
Second Rule: VPN to LAN
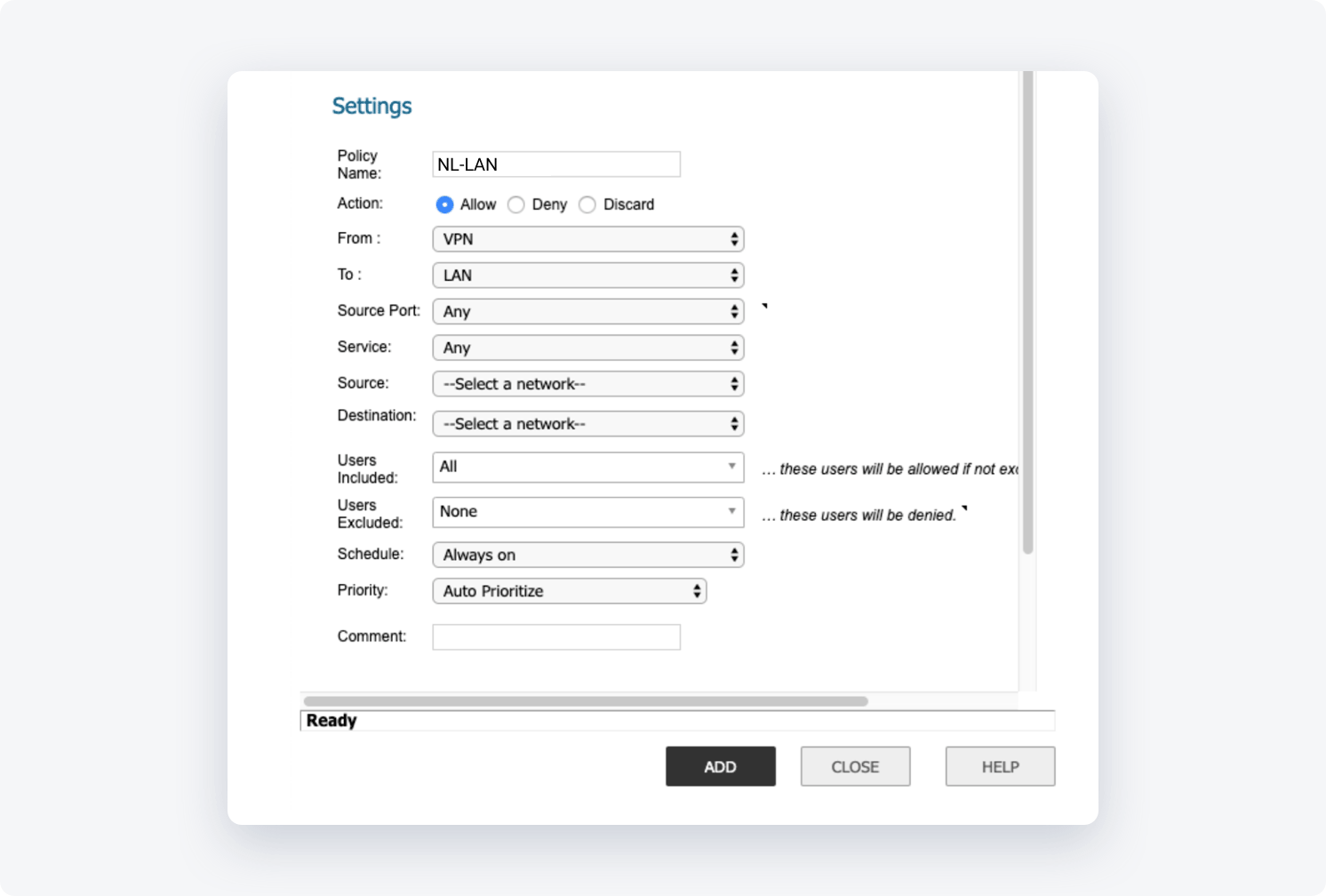
- Policy Name: NordLayer-LAN
- Action: Allow
- From: VPN
- To: LAN
- Source Port: Any
- Service: Any
- Source: NordLayer: Network object
- Destination: Your internal subnet object
- Select Add.
Site-to-Site creation
Go to VPN
Under Base Settings add VPN Policy; Open General Tab:
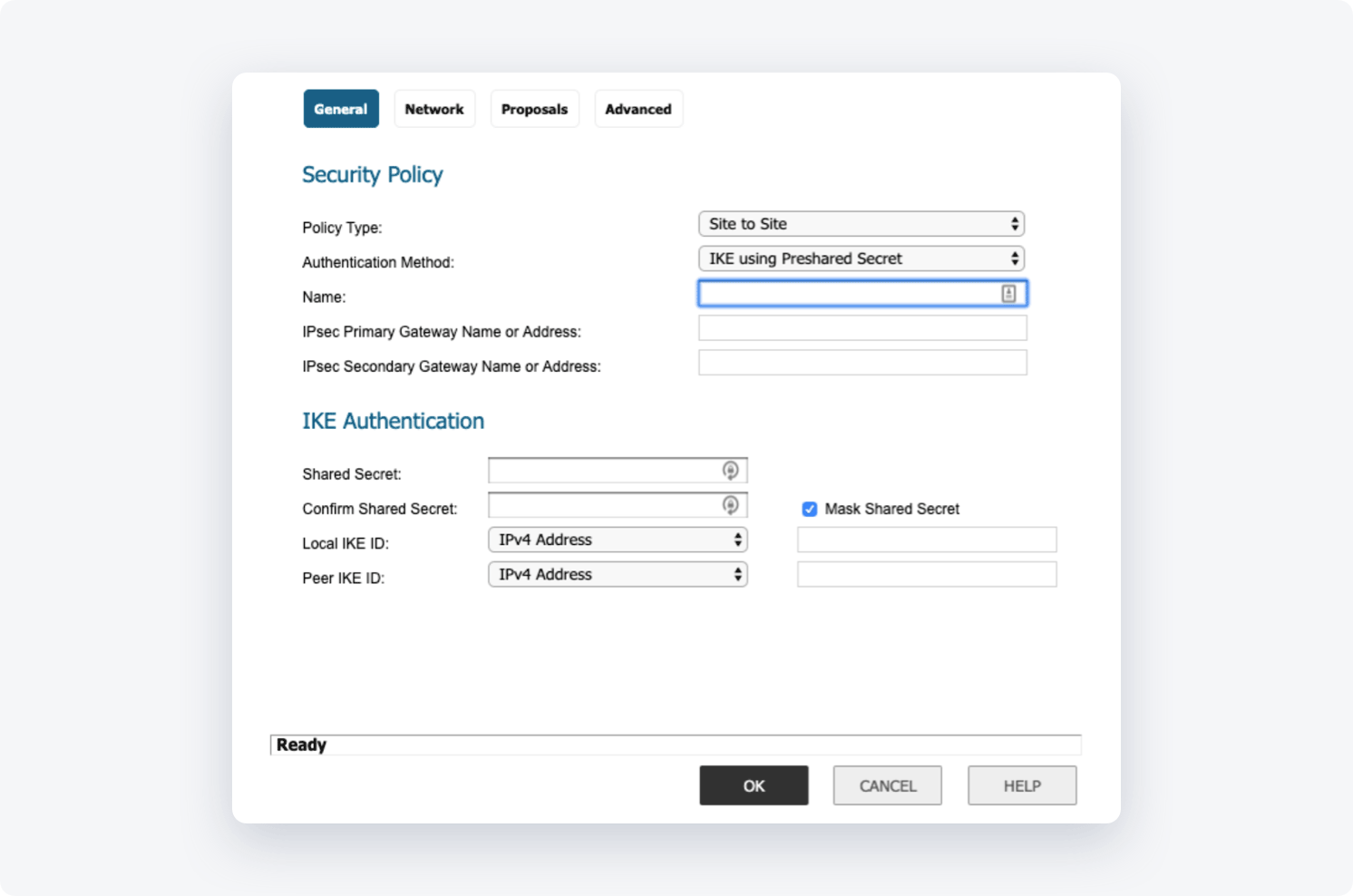
Security Policy
- Policy Type: Site to Site
- Authentication Method: IKE using Preshared Secret
- Name: Give it name ex. "NordLayer-Office"
- IPsec Primary Gateway Name or Address: put your NordLayer gateway address
- IPsec Secondary Gateway Name or Address: leave blank
IKE Authentication
- Shared Secret: generate a key (we will also need this value on our end)
- Confirm Secret: put the secret again
- Local IKE ID: "IPv4 Address: put your public office IP address
- Peer IKE ID: "IPv4 Address:" put the IP of your NordLayer dedicated server
Network Tab
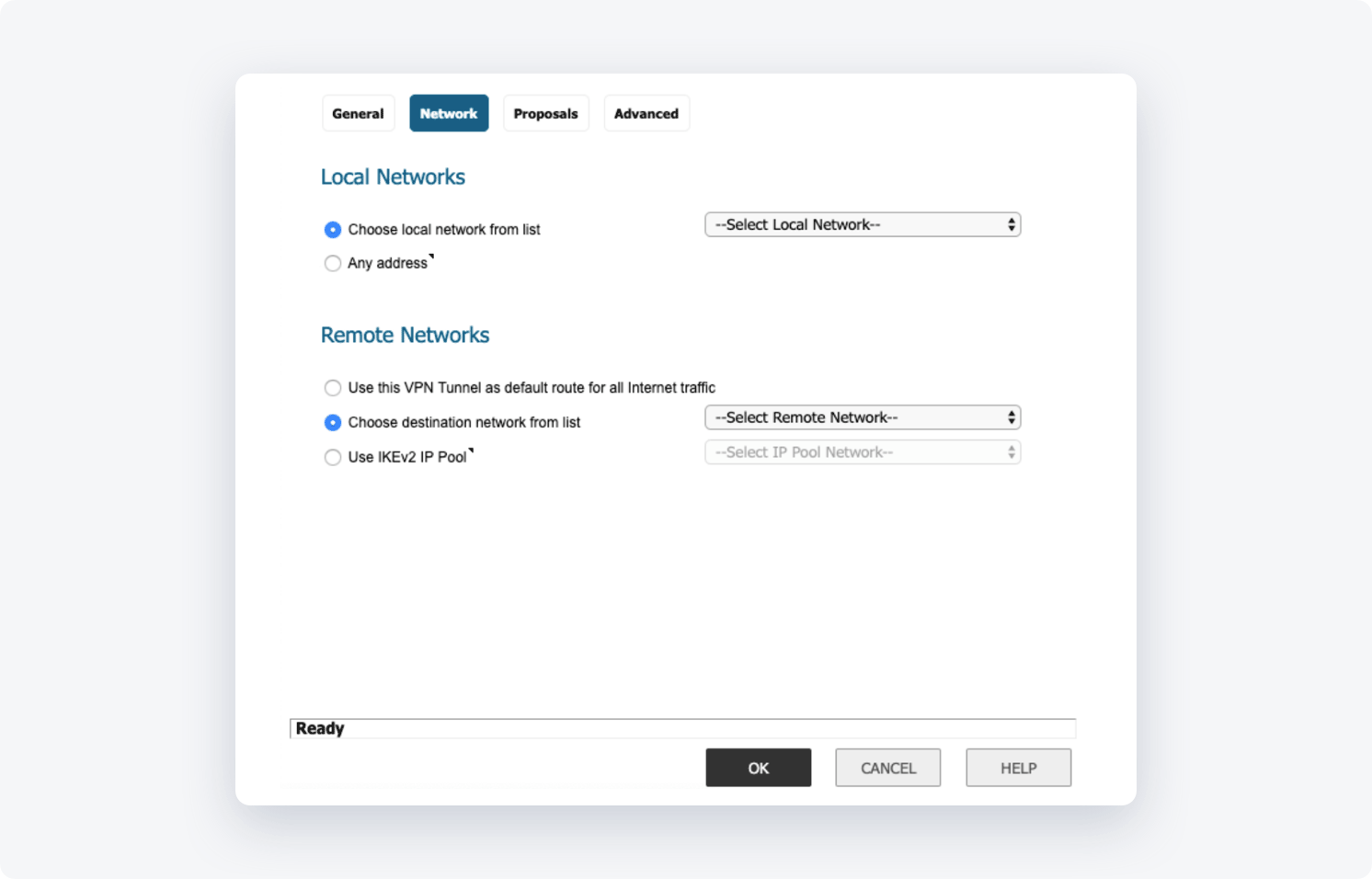
Local Networks
- Select a local network from the list: choose your local network object
Remote Networks
- Select the destination network from the list: choose NordLayer-Network object
Proposals Tab

IKE (Phase 1) Proposal
- Exchange: Main Mode
- DH Group: Group 2 (Group 14 recommended if your device supports it)
- Encryption: AES-256
- Authentication: SHA1 (SHA256 recommended if your device supports it)
- Life Time (seconds): 3600
IPsec (Phase 2) Proposal
- Protocol: ESP
- Encryption: AES-256
- Authentication: SHA1 (SHA256 recommended if your device supports it)
- Mark v for "Enable Perfect Forward Security"
- DH Group: Group 2 (Group 14 recommended if your device supports it)
- Life Time (seconds): 28800
Advanced Tab
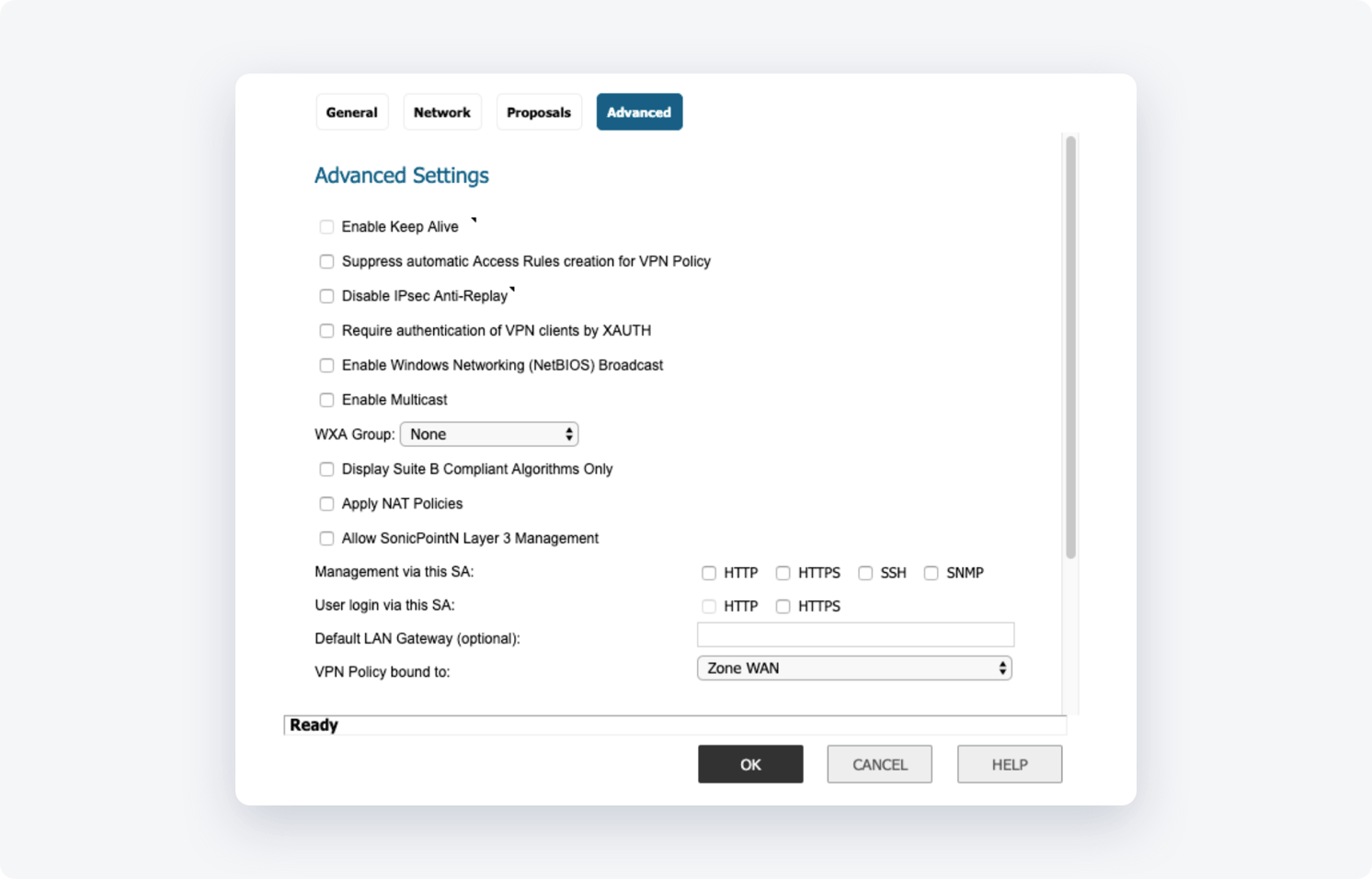
Advanced Setting
Mark v in Enable Keep Alive.
Select OK to create the new VPN Policy
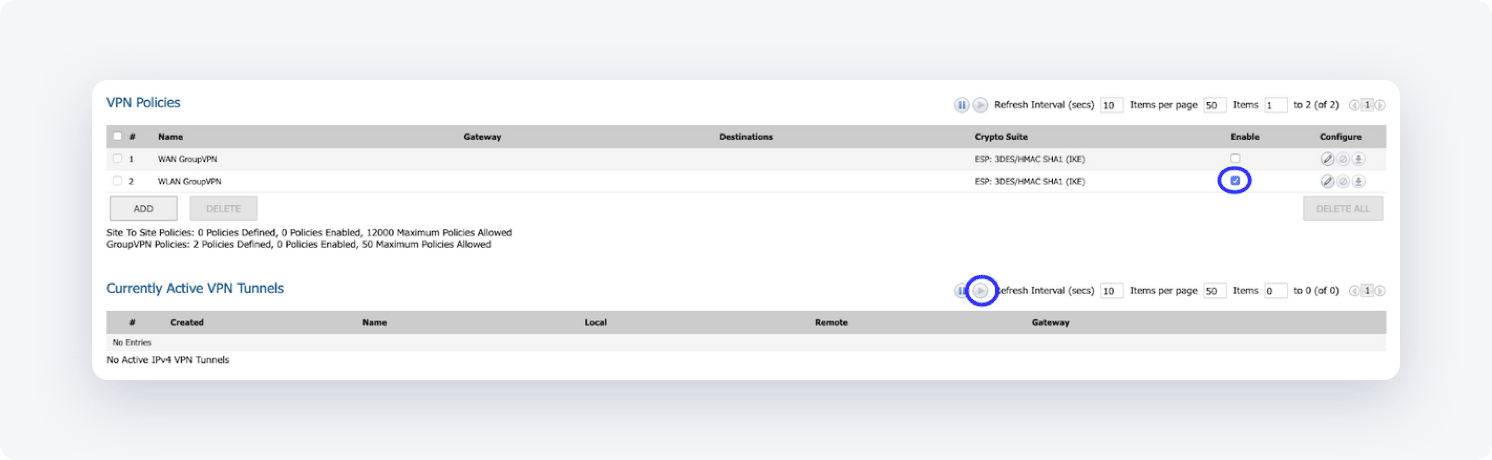
Make sure the new Policy you created is enabled.
You can select the play button right to the Currently Active VPN Tunnels and you should see that your new tunnel is up.
If the tunnel won't start you should go to Event Logs and look for errors regarding the new VPN policy you created.
Ending note:
In order to finalize the site-to-site setup on our end, please provide these values via Site-to-site request from in the NordLayer Control Panel:
- Pre-shared key - you can generate it or we can provide it
- Encryption details (AES, SHA and DH group) - AES256, SHA256 and DH group 14 are recommended (also must support IKEv2)
- Remote gateway/router public IP (must be reachable while connected to the dedicated server)
- Remote subnet and mask (the subnet is used in your local network)
Note: In case you are experiencing different results, make sure that you have you carefully gone through all the steps. Having said that, in case the issue persists please feel free to contact our 24/7 customer support team.

