- 3 Minutes to read
How NordLayer works
- 3 Minutes to read
Why do you need NordLayer?
We understand that modern businesses require more from their security solution than what is currently offered in today’s market. Alone, Business VPN technology - whilst still an integral part of an overall security setup - does not provide the protection and security our client’s remote workforces and company data deserves.
NordLayer allows you to set granular access permissions through network control features so businesses like yours can be safe knowing their sensitive cloud data is secure and restricted to authorized users only.
How does it work?
NordLayer works through a series of security layers that when utilized together, they protect users and ensure secure access across the entire corporate network:
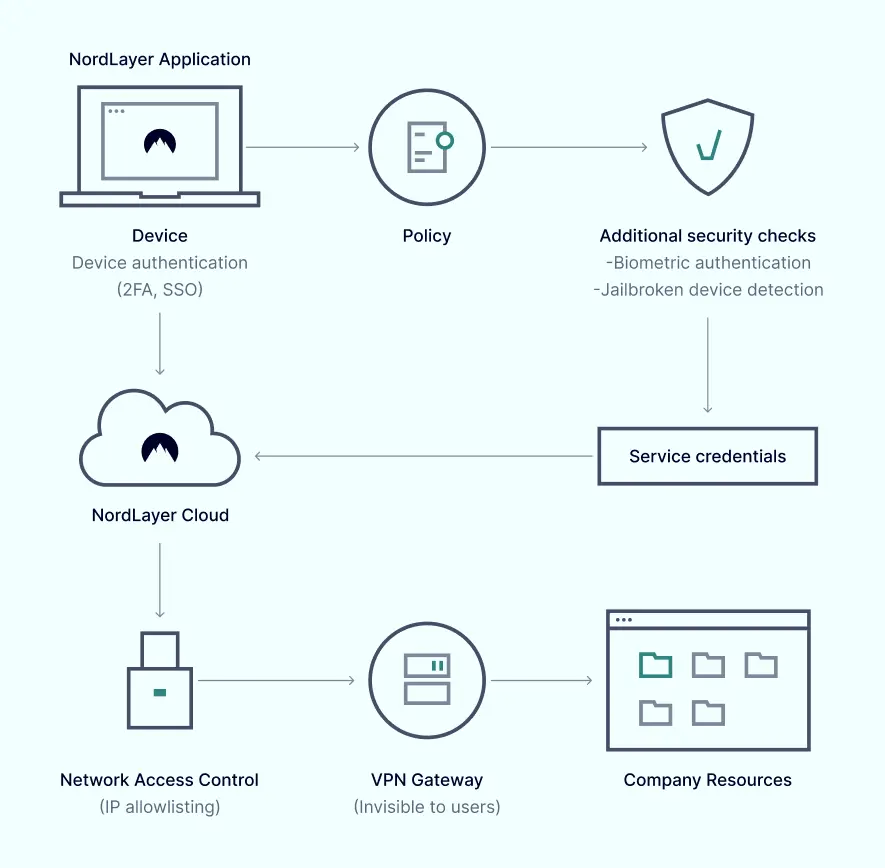
Secure access to the NordLayer application
Once you’ve safely logged on to your device, secure logins must be used to gain access at the application level. NordLayer’s multi-factor authentication features like 2FA and Single-Sign-On (SSO), enable the first layer of secure protection for users when using the service:
- Strengthen security — Having a second identification level drastically reduces the risk of malicious users gaining access to your devices or sensitive information.
- Keep remote workers safe — Multi-factor authentication allows employees to access company resources from any device with complete safety, whatever their location.
- Limit unnecessary admin — Responsibility of password management is removed from IT admins with users able to do this themselves.
Implement team and user policies
Using NordLayer, you can build teams for network segmentation, assign user permissions, and create gateways based on employee trust level.
- Increase access limitations — Creating team gateways allows users to only access specific network resources they need to fulfil their roles and nothing more.
- Improve visibility — NordLayer gives you full insight into who and what is accessing which areas of the company network.
- Implement Biometrics at this point for additional security — fingerprint or face ID verification. NordLayer can also detect jailbroken or rogue iOS devices.
Hide data and manage user activity
Connect to company applications, resources and data via a NordLayer secure tunnel. The tunnel works to encrypt transferred data and network activity from any unknown and untrusted users.
- Hide activity — Through NordLayer’s military grade encryption, all activity on the network remains invisible to users outside of the network perimeter.
- Protect transferred data packages — With all data and activity hidden, the likelihood of data being intercepted or leaked is significantly reduced.
Gain complete access control
Network segmentation is ensured with users assigned to specific gateways — each with unique team access permissions. Using NordLayer’s IP allowlisting also enables admins to set specific user permissions so users can only access the resources relevant to their job role.
- Permission-based access — Set user permissions based on employee trust level, to make sure their permissions stretch to what they need to access to fulfil their work.
- Trusted users only — Create a bespoke allow list with trusted user IP addresses to granulate access permissions and segment areas of your network.
Without NordLayer
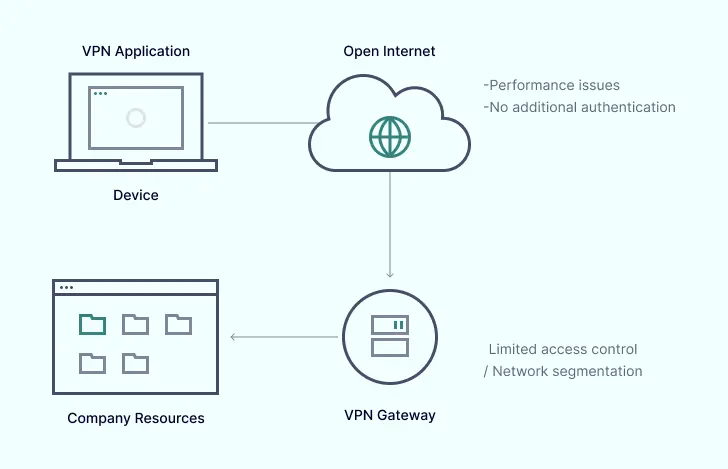
Many legacy solutions handling the needs of a business network may now be unfit for purpose by today’s cybersecurity standards — often having limited capability and running at suboptimal performance. Without the protection and adaptability that NordLayer provides, your company could unknowingly be leaving the network underperforming, and your data and resources vulnerable to exposure.
- Lower speed & reliability — A personal VPN utilizes a single tunnel to handle all user traffic. For businesses using this service for all employees, performance issues will occur including reduced speed and increased latency.
- Increased visibility — Legacy VPN gateways are public. Therefore, they have a higher risk of being exposed to malicious attacks. Businesses can mitigate this risk with a more advanced network access solution, which hides dedicated gateways from outside users.
- Difficult to scale & maintain — Modern network access solutions like NordLayer are quick to install and manage. Without features like a centralized Control Panel, and easy license transferability, managing and scaling users across the business becomes an unnecessary obstacle to overcome.
Combining layers of protection into one easy-to-use solution - NordLayer - provides businesses with all of the tools to achieve complete network security. Built on Zero Trust principles, NordLayer security solutions help organizations of all sizes to fulfill scaling and integration challenges when building a modern secure remote access solution, within an ever-evolving SASE framework.
Note: For further information on how your business can benefit from NordLayer’s features and solutions, please reach out to our 24/7 customer support team.

