Note: If your device/service supports SHA256 and DH group 14, it is recommended to use these settings instead.
Please note, the choice between Transit Gateway or a simple Virtual Gateway depends on your AWS architecture. If you are not sure, we encourage you to visit AWS's official documentation.
Creating the Transit Gateway
- Go to the VPC section in the AWS Console
- Under the left panel, select Transit Gateways
- Click on Create transit gateway at the top
.png)
- Fill in the following details:
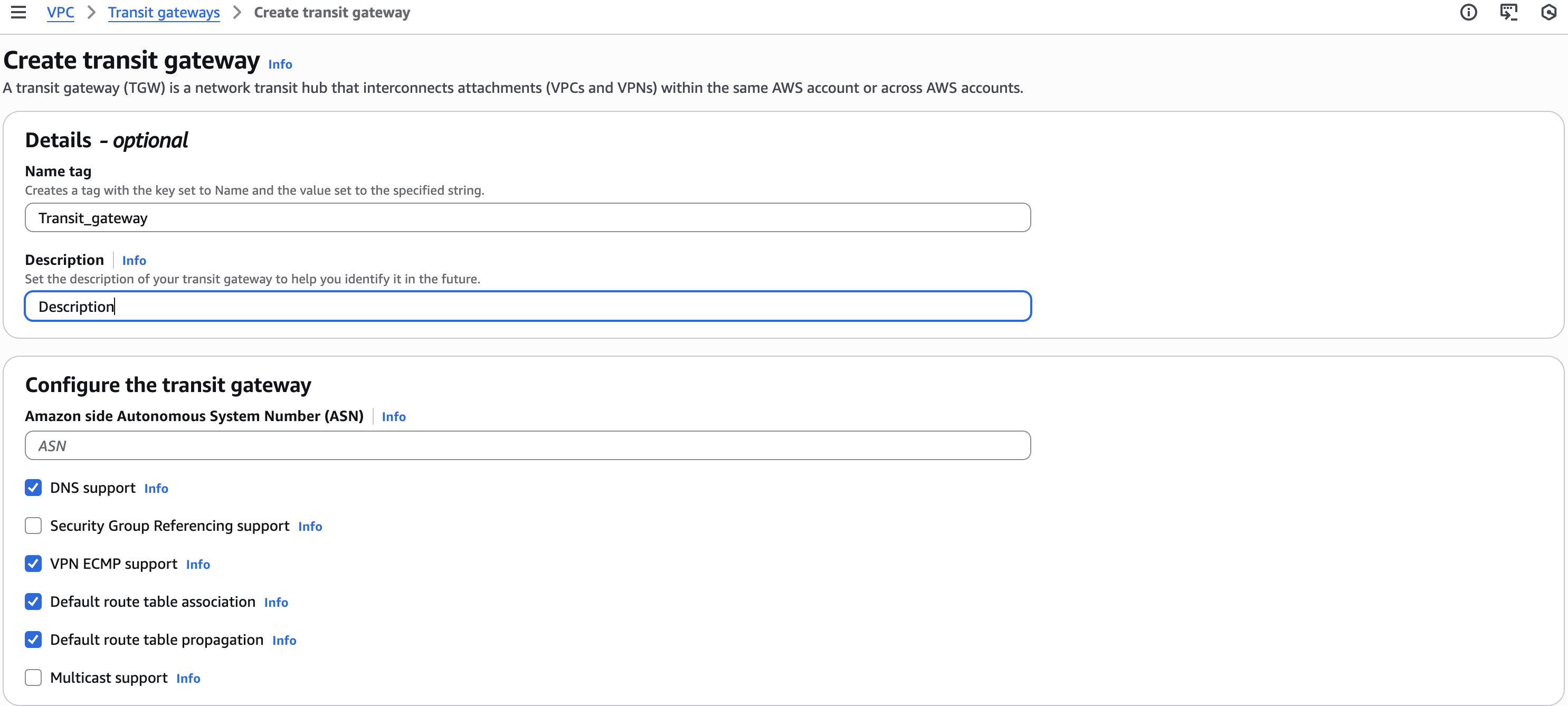
- Name tag - Insert the name of the Transit Gateway
- You can keep the default parameters for the rest of attributes
- Click on Create transit gateway
Creating the Transit Gateway attachments
- On the left pane, select Transit Gateway Attachments
- Click on Create transit gateway attachment at the top
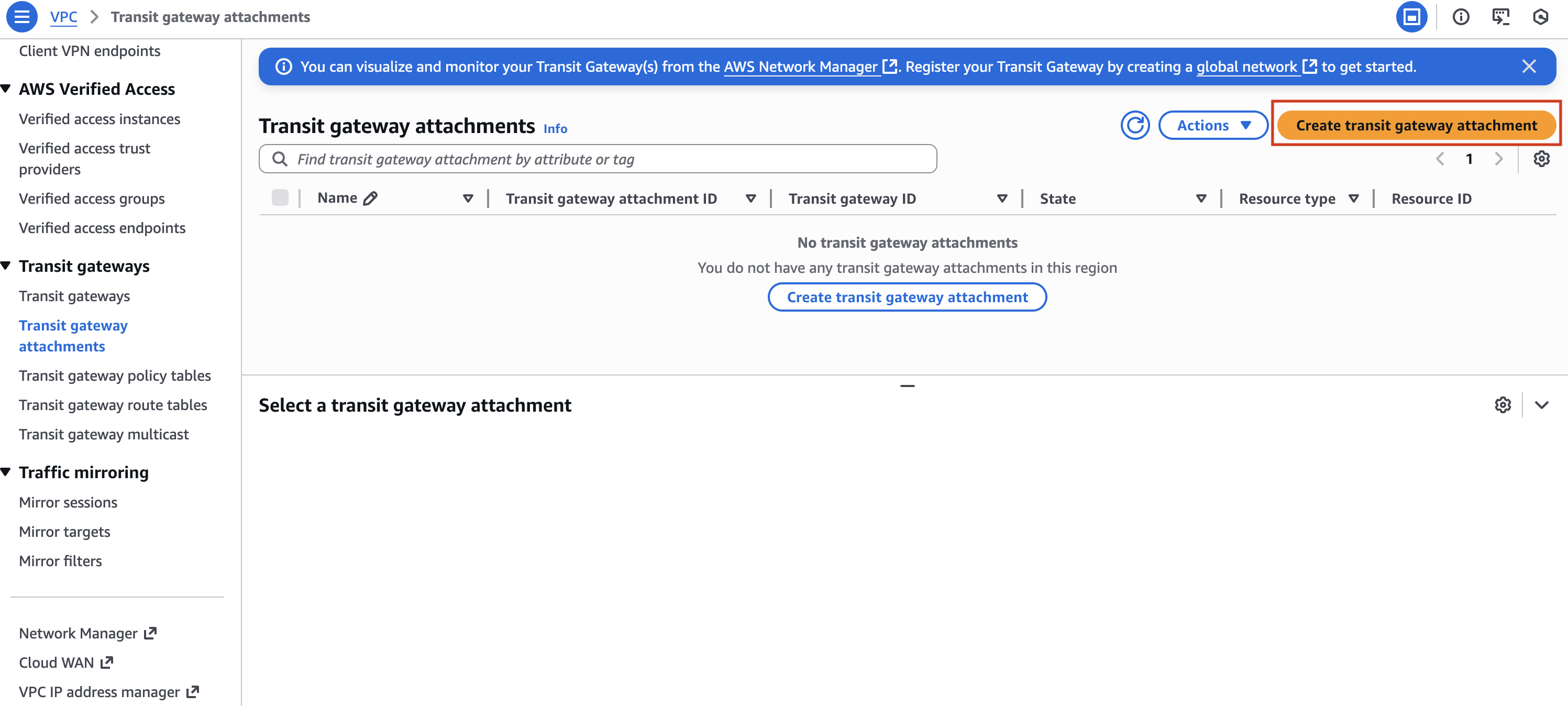
- Fill in the following information and select Create transit gateway attachment
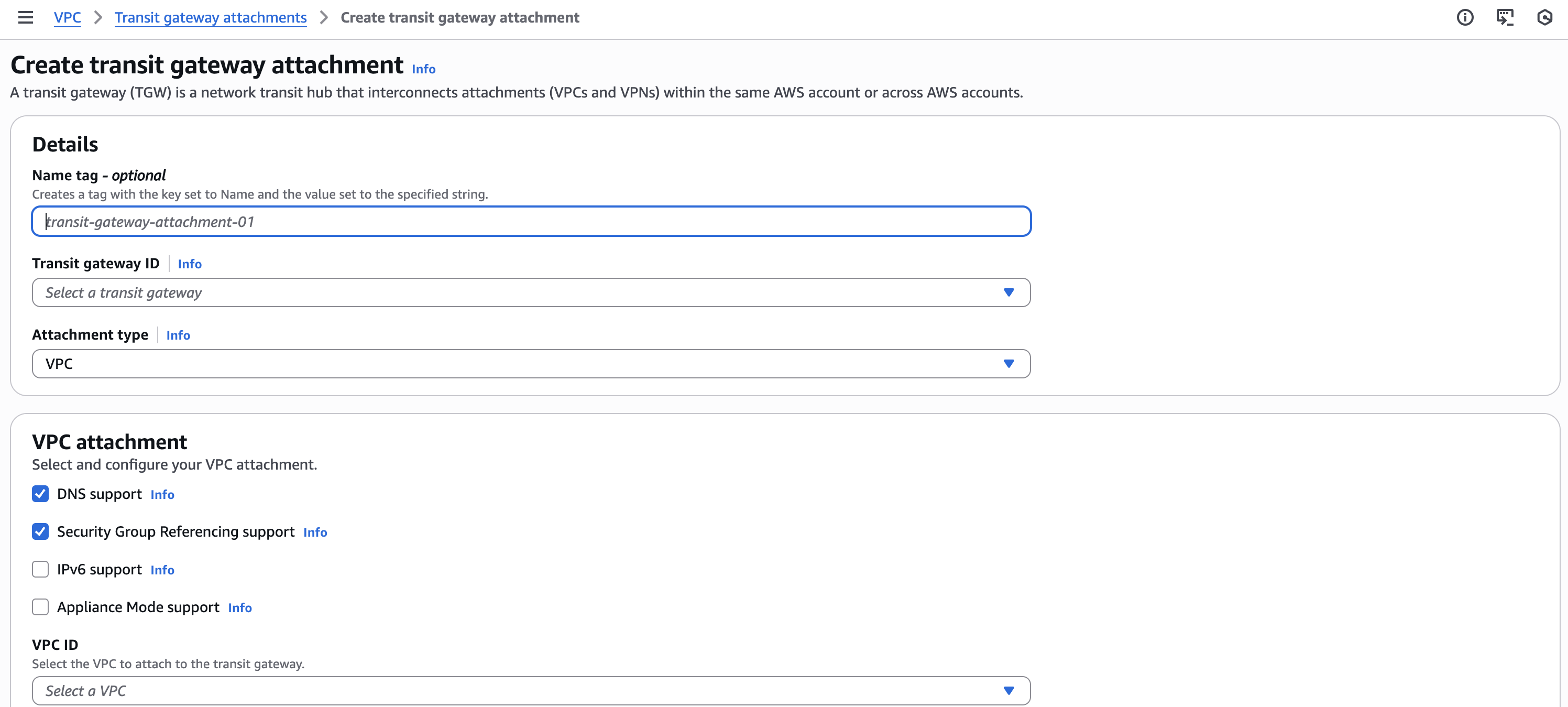
- Name tag: Insert the name of the Transit Gateway Attachment
- Transit gateway ID: Pick the newly created Transit gateway
- Attachment Type: VPC
- VPC ID: Select the relevant VPC
- You can keep the other attributes in their default values
Note: Please repeat the above procedure for each of the VPCs that you would like to gain access to.
Creating the Transit Gateway VPN attachment
- Click on Create transit gateway attachment at the top

- Fill in the following details
.png)
- Transit Gateway ID: Choose your newly created Transit Gateway
- Attachment type: VPN
- Customer Gateway ID: New
- IP Address: the IP address of your NordLayer server with a dedicated IP
- BGP ASN: Leave default values
- Routing Options: Static
- For the other attributes, leave them in their default values
- Click on Create transit gateway attachment
Note: This may take several minutes
Configuring the routing on AWS platform
- Go to the VPC section in the AWS Console. Under Transit Gateways, select Transit Gateway Route Tables
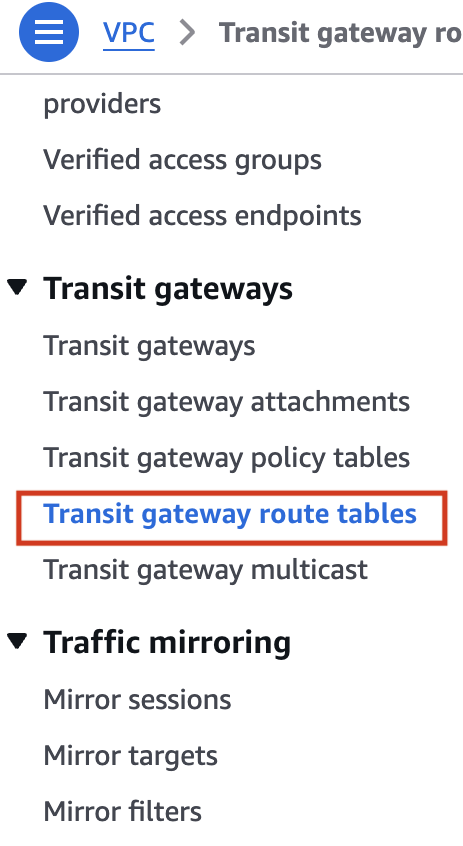
Choose the relevant Transit Gateway Route Table record
On the bottom, choose Propagations
.png)
Verify that all of the Transit Gateway Attachments are included. If you have 2 VPCs, this is how it should look like:
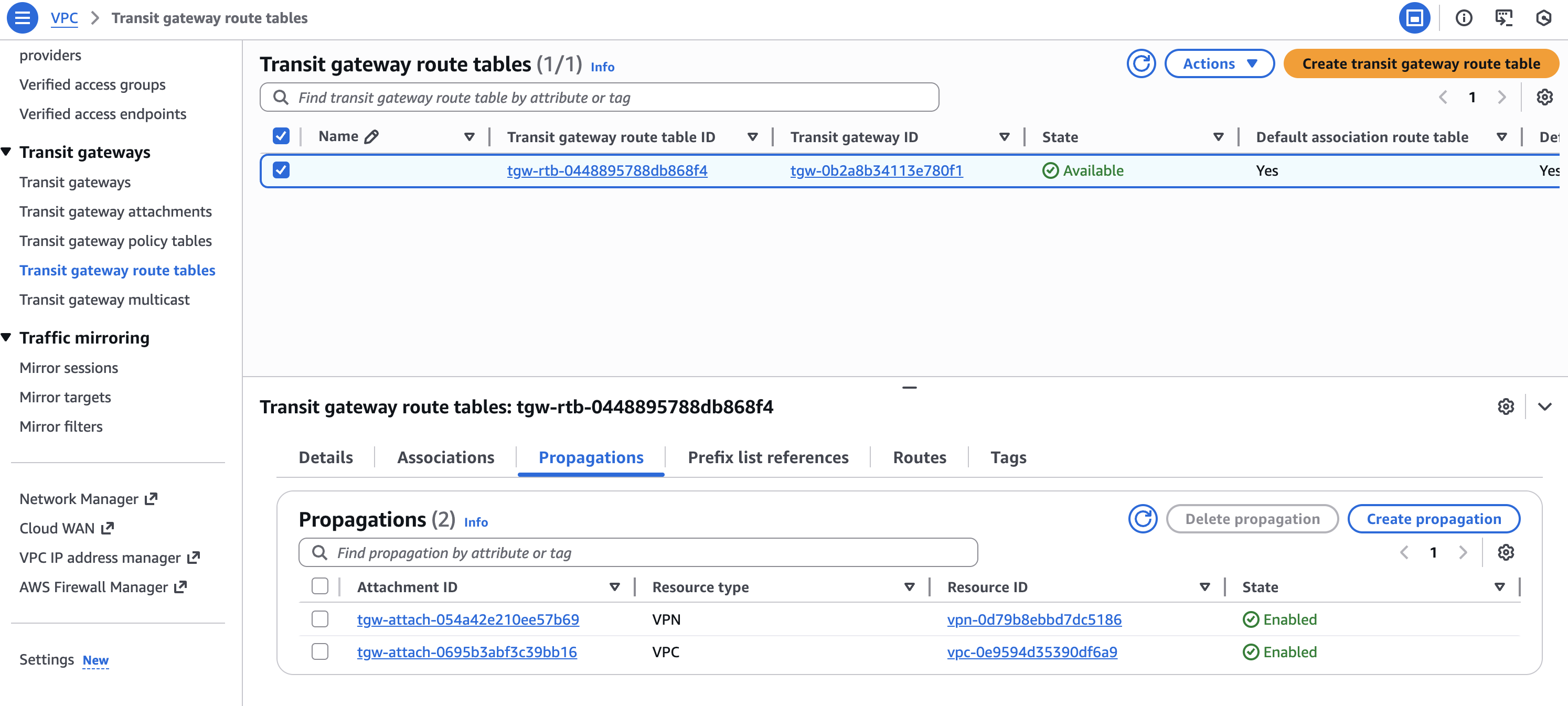
In case one of the Transit Gateway Attachments is missing, click on Create propagation and add the missing record(s).
On the bottom, select Associations
Verify that all of the Transit Gateway Attachments are included (same as step 4)
At the bottom, near the Propagations tab, select Routes

Click on Create static route and fill in the following details:
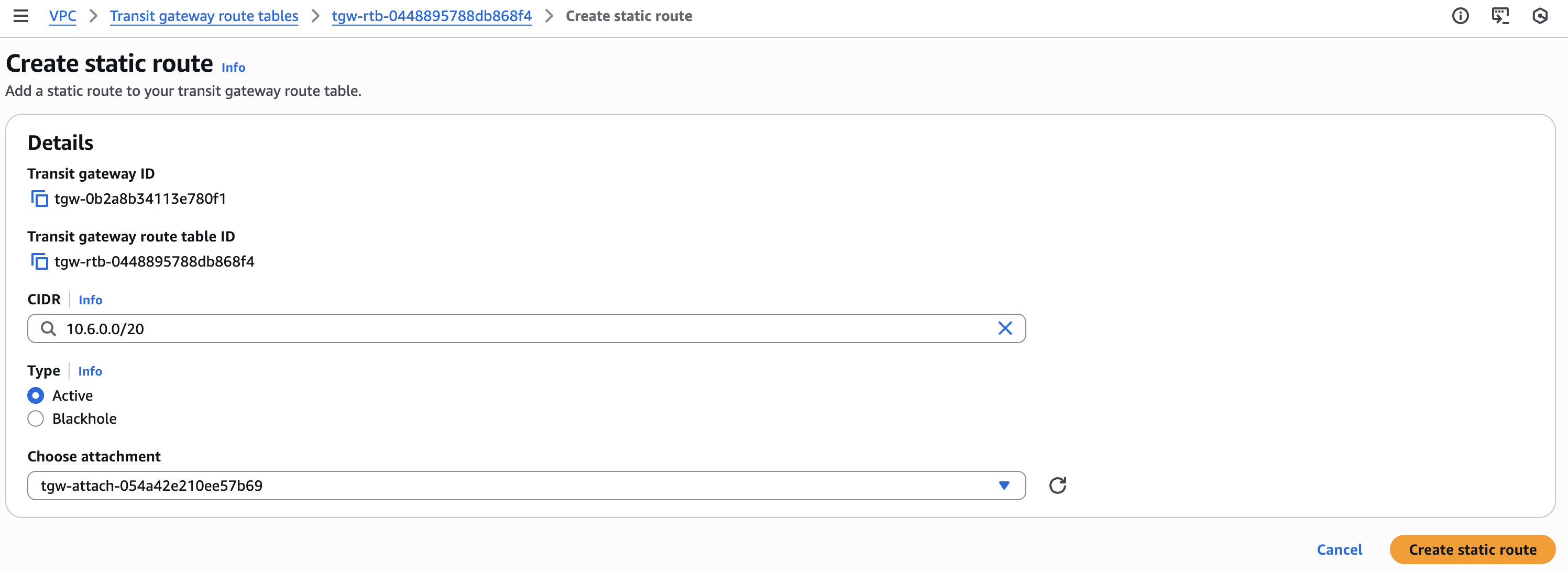
- CIDR: Insert the NordLayer subnet, which is 10.6.0.0/20
- Choose attachment: Choose the VPN attachment
- On the left side, under Virtual Private Cloud, click on Route Tables
Select the Route Table for one of the attached VPCs
On the bottom, click on Routes
Click on Edit Routes, in a newly opened window select Add route and fill in the following details:
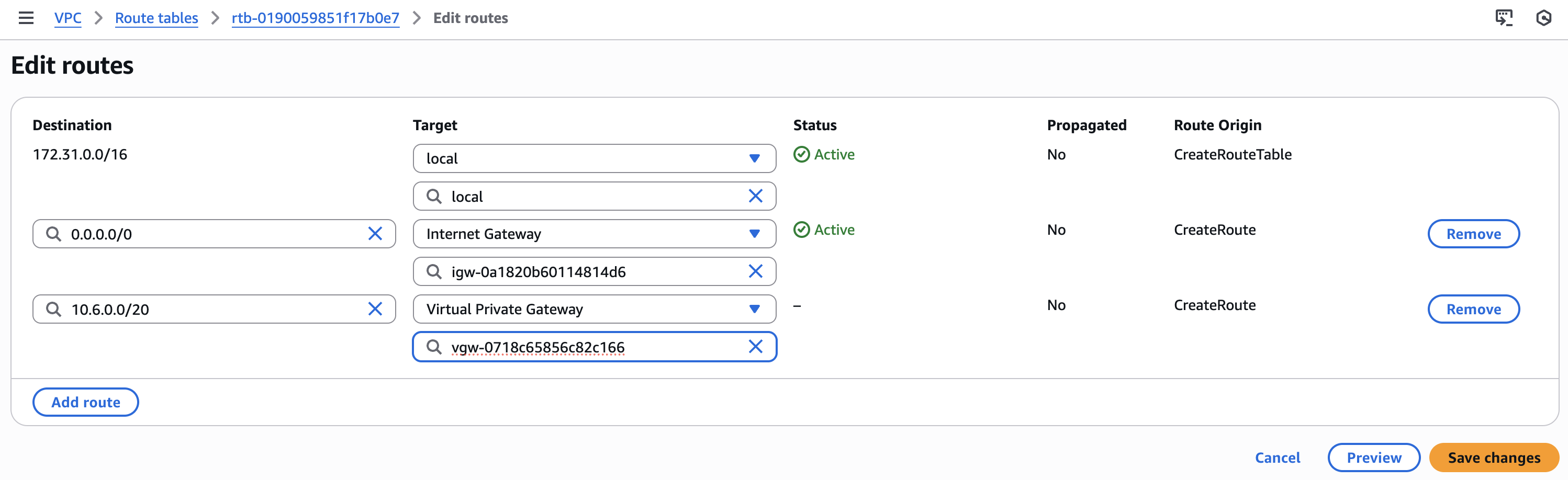
- Destination: Your NordLayer network subnet - 10.6.0.0/20
- Target: Choose Transit Gateway and pick the relevant Transit Gateway
- Click on Save changes
Repeat the steps 10-12 for other attached VPCs.
Collecting the tunnel configuration from the AWS Console
- Return to Site-to-Site VPN Connections and select Download Configuration
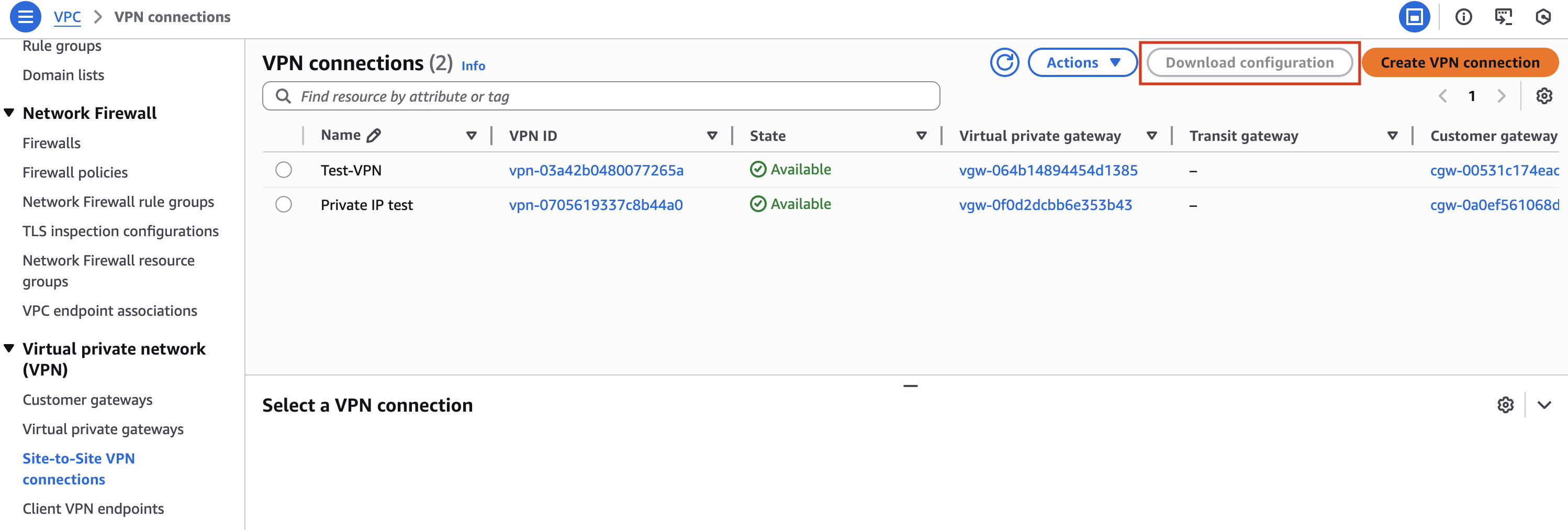
- Fill in the following details and click on "Download".
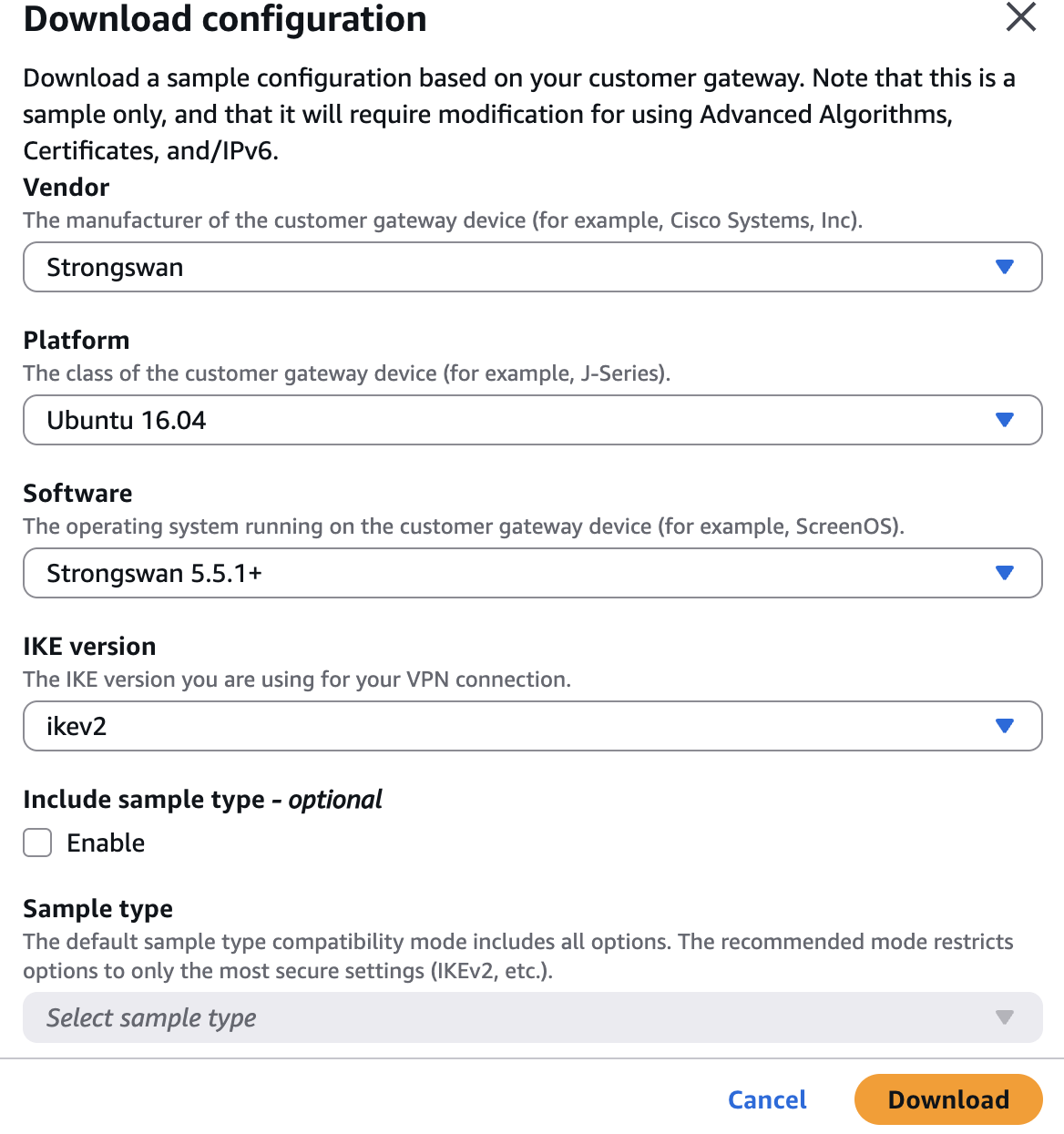
Obtain IPSEC Tunnel #1 details
- Open the configuration file which you have just downloaded and scroll until conn Tunnelid as shown in the screenshot below:
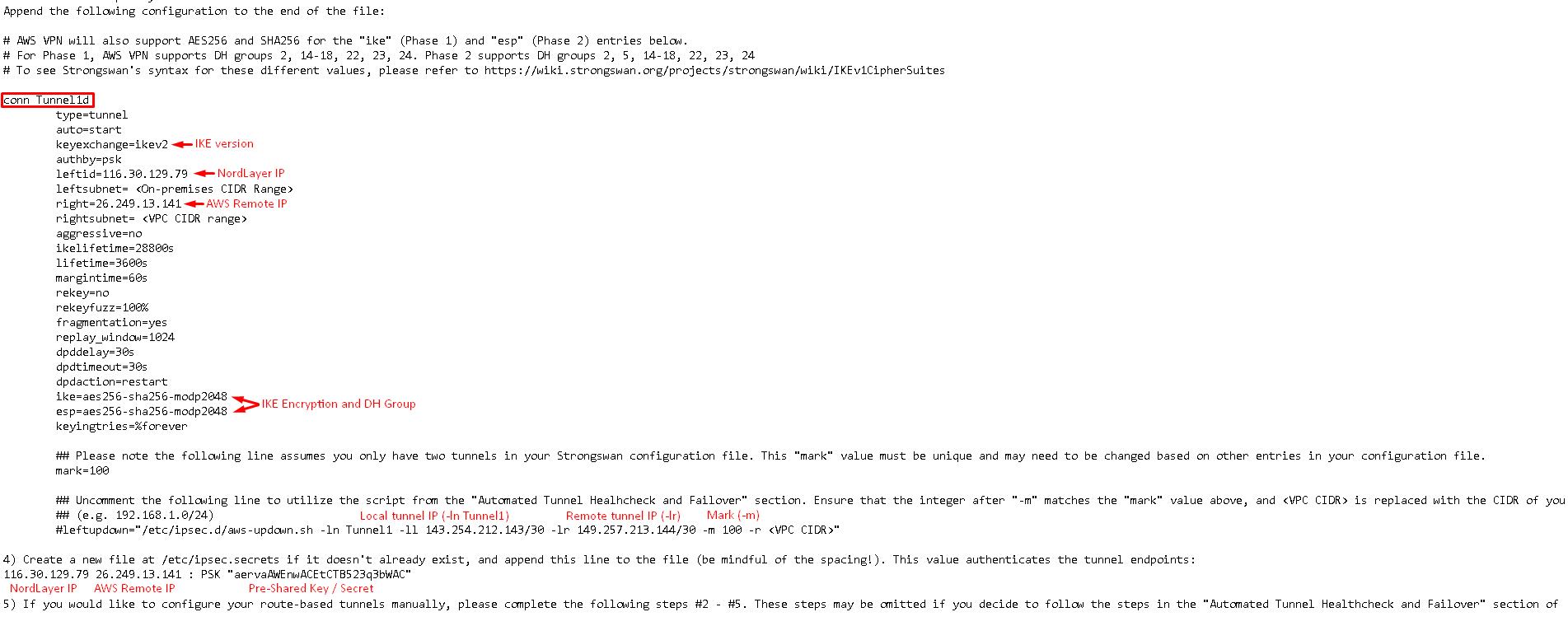
- Make a note of these details as they will be needed for the VPN server configuration:
- IKE version: IKEv2 (recommended)
- Remote IP (right): Your AWS Remote IP
- Encryption settings IKE Encryption and DH Group
- Local IP (-ll): Local Tunnel IP
- Remote IP (-lr): Remote Tunnel IP
- Mark (-m): specified in the config
- Pre-shared key (PSK): Your Pre-Shared Key / Secret
Obtain IPSEC Tunnel #2 details
- Within the same configuration file, scroll down to locate the section labeled conn Tunnel2.
- Take note of the following details as they will be required for configuring Site-to-Site connection:
- IKE version: IKEv2 (recommended)
- Remote IP (right): Your AWS Remote IP
- Encryption settings IKE Encryption and DH Group
- Local IP (-ll): Local Tunnel IP
- Remote IP (-lr): Remote Tunnel IP
- Mark (-m): specified in the config
- Pre-shared key (PSK): Your Pre-Shared Key / Secret
Submitting Site-to-Site request form
Once you have obtained all necessary details from the AWS config – IPSEC Tunnel #1 and IPSEC Tunnel #2 – please proceed next by submitting our Site-to-site Request from.
Note: In case you are experiencing different results, make sure that you have you carefully gone through all the steps. Having said that, in case the issue persists please feel free to contact our 24/7 customer support team.